After reports of active exploitation of CVE-2025-61882, an Oracle E-Business Suite flaw leveraged in recent Cl0p data theft attacks, another critical issue has surfaced in Fortra GoAnywhere software. The newly disclosed vulnerability, tracked as CVE-2025-10035, allows unauthenticated command injection and RCE and has already been weaponized by the Storm-1175 threat group to deploy Medusa ransomware.
Detect CVE-2025-10035 Exploitation Attempts Linked to Storm-1175
With more than 35,000 new vulnerabilities recorded by NIST in 2025, cybersecurity teams are facing an intense race against time. As vulnerability exploitation continues to dominate as the primary attack vector and threats become increasingly advanced, proactive detection is of paramount importance to keep up with the attacker’s pace.
Register now for the SOC Prime Platform to reach an extensive collection of curated detection content and AI-native threat intelligence, helping your team outscale sophisticated offensive campaigns that leverage vulnerability exploits to compromise systems. SOC Prime team has recently released a new Sigma rule addressing the latest CVE-2025-10035 exploitation attempts linked to the Storm-1175 adversary activity.
Possible GoAnywhere Managed File Transfer CVE-2025-10035 Exploitation Patterns (via cmdline)
This Sigma rule is aligned with the MITRE ATT&CK® framework, addressing the Initial Access tactic and the Exploit Public-Facing Application technique (T1190). The rule can be used across 30+ SIEM, EDR, and Data Lake platforms to accelerate detection engineering procedures across multiple environments.
To access the comprehensive detection stack addressing this threat and help your organization reduce the risk of exposure, click the Explore Detections button:
For a broader range of SOC content for vulnerability exploit detection, security engineers can also apply the “CVE” tag.
Security engineers can also leverage Uncoder AI, an IDE and co-pilot for detection engineering. With Uncoder, defenders can instantly convert IOCs into custom hunting queries, craft detection code from raw threat reports, generate Attack Flow diagrams, enable ATT&CK tags prediction, leverage AI-driven query optimization, and translate detection content across multiple platforms. For instance, cyber defenders can instantly convert IOCs from the latest Microsoft Threat Intelligence team report into custom IOC queries ready to run in the chosen SIEM or EDR environment.
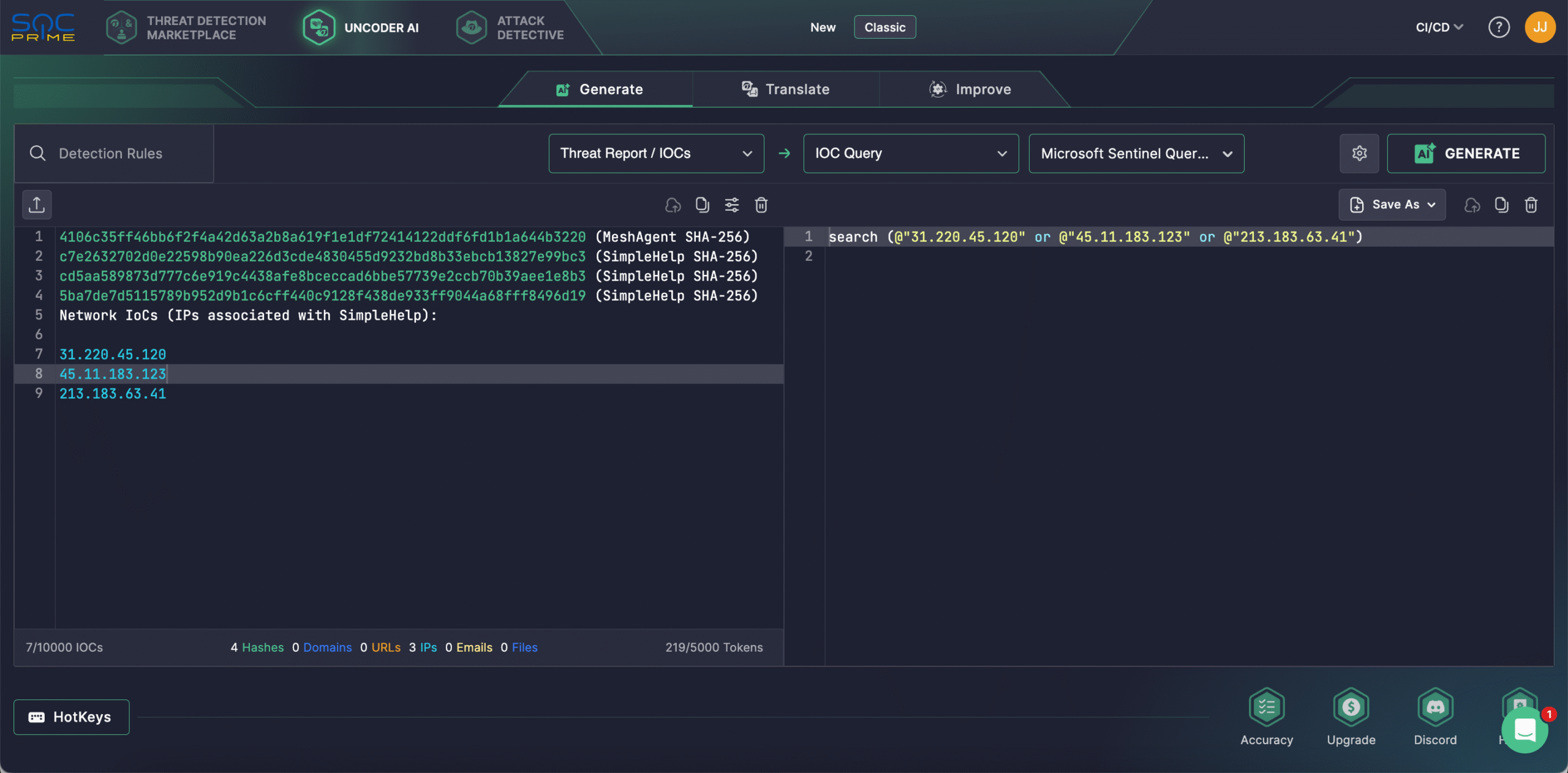
Alternatively, security professionals might leverage the New Uncoder AI mode, enhanced with Chat Bot functionality and MCP tools support, to generate an Attack Flow diagram in a few clicks.
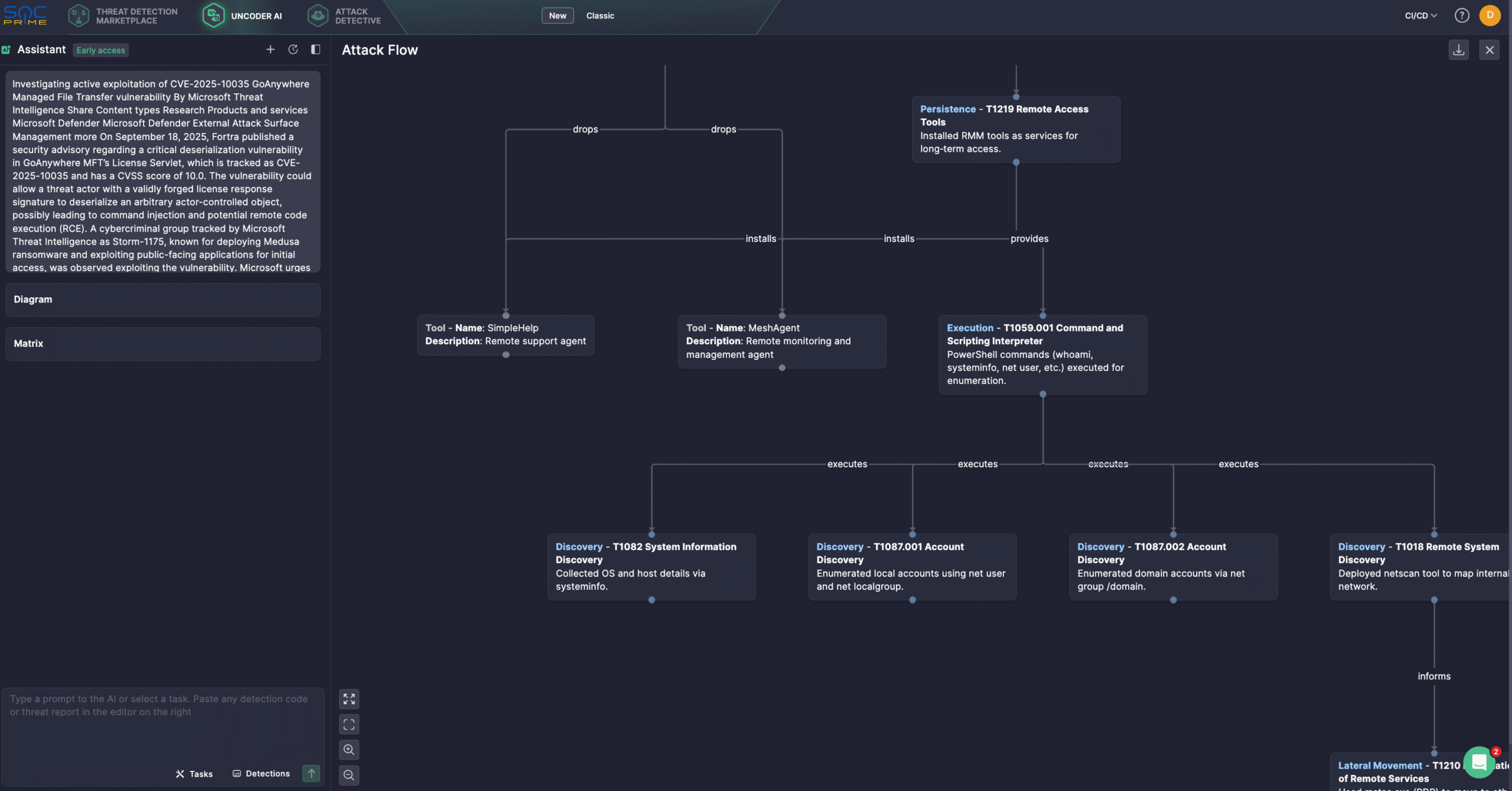
CVE-2025-10035 Analysis
On September 18, 2025, Fortra released a security advisory detailing a critical vulnerability in GoAnywhere Managed File Transfer (MFT) License Servlet, tracked as CVE-2025-10035 with the highest CVSS score of 10.0. The flaw allows an attacker to craft a forged license response signature, enabling the deserialization of arbitrary, attacker-controlled objects that could lead to command injection and potentially to RCE.
Microsoft Threat Intelligence team has attributed the active exploitation of this vulnerability to the Storm-1175 group, known for deploying Medusa ransomware and exploiting public-facing applications for initial access. The vulnerability affects software versions up to 7.8.3, where attackers can bypass signature verification by manipulating the license response mechanism.
Researchers have observed exploitation activity in multiple organizations, with the earliest related incidents dating to September 11, 2025. Storm-1175’s multi-stage attack chain began with exploiting the zero-day flaw for initial access, followed by persistence through SimpleHelp and MeshAgent remote RMM tools dropped under the GoAnywhere MFT process. The attackers also created .jsp web shells within the MFT directories alongside these RMM payloads.
Subsequent activity included user and system reconnaissance, network scanning with netscan, and lateral movement via mstsc.exe. For C2, adversaries used the deployed RMM tools and established Cloudflare tunnels for encrypted communications. In the exfiltration stage, Rclone was executed to extract data, with at least one confirmed case of Medusa ransomware deployment.
Successful exploitation could allow unauthenticated attackers—if able to craft or intercept valid license responses—to achieve command injection and RCE on vulnerable systems, making this issue highly dangerous for internet-exposed GoAnywhere instances. Once compromised, attackers can perform system and user discovery, maintain persistence, and deploy additional tools for lateral movement and ransomware payloads.
Potential CVE-2025-10035 mitigation measures to minimize the exploitation risks include applying patches immediately following Fortra’s recommendations. Still, upgrading does not address previous exploitation activity, and a review of the impacted system may be required. This includes auditing license verification mechanisms and closely monitoring GoAnywhere environments for unusual activity to reduce exposure to the threat.
The escalating threat of CVE-2025-10035 exploitation, coupled with attackers’ month-long lead time and confirmed ransomware deployment, underscores the urgent need for heightened cybersecurity vigilance and proactive defense measures. SOC Prime curates a complete product suite backed by AI, automated capabilities, and real-time threat intelligence, equipping defenders with cutting-edge technologies to preempt cyber-attacks at their earliest stages while optimizing operational costs and improving scalability.




