Security heads-up for cyber defenders! Microsoft has recently fixed a critical elevation of privilege vulnerability (CVE-2023-23397) affecting Microsoft Outlook for Windows that allows adversaries to dump hash passwords from targeted instances. Notably, the flaw has been exploited in the wild as a zero-day since April 2022, being utilized in cyber-attacks against the government, military, and critical infrastructure organizations across Europe.
CVE-2023-23397 Detection
With the ever-increasing number of security flaws affecting widely used software products, proactive detection of vulnerability exploitation has been among the top security use cases in 2021-2022 and still holds the leading position. The infamous privilege escalation vulnerability tracked as CVE-2023-23397 with a 9.8 severity rating based on the CVSS score impacts all versions of Microsoft Outlook. Being actively exploited in the wild, this Microsoft Outlook vulnerability, when abused by attackers, can pose a serious threat to organizations that rely on these popular Microsoft products. To help organizations timely spot adversary activity and proactively detect the CVE-2023-23397 exploitation patterns, SOC Prime Team has recently released relevant Sigma rules. Follow the links below to instantly reach these detections mapped to the MITRE ATT&CK framework v12 and instantly convertible to the industry-leading SIEM, EDR, and XDR solutions.
Possible Microsoft Outlook [CVE-2023-23397] Exploitation Patterns (via process_creation)
This Sigma rule addresses the Credential Access tactic with the Forced Authentication (T1187) used as its primary technique.
Outlook Used to Open Stand-Alone Message File with Suspicious Location (via cmdline)
The above-referenced Sigma rule also addresses the Credential Access tactic with the Forced Authentication (T1187) technique along with the Initial Access tactic represented by the Phishing (T1566) technique.
By clicking the Explore Detections button, organizations can gain instant access to even more detection algorithms aimed to help identify the malicious behavior linked to the exploitation attempts of CVE-2023-23397 that can potentially affect their Microsoft Outlook instances. For streamlined threat investigation, teams can also drill down to relevant metadata, including ATT&CK and CTI references.
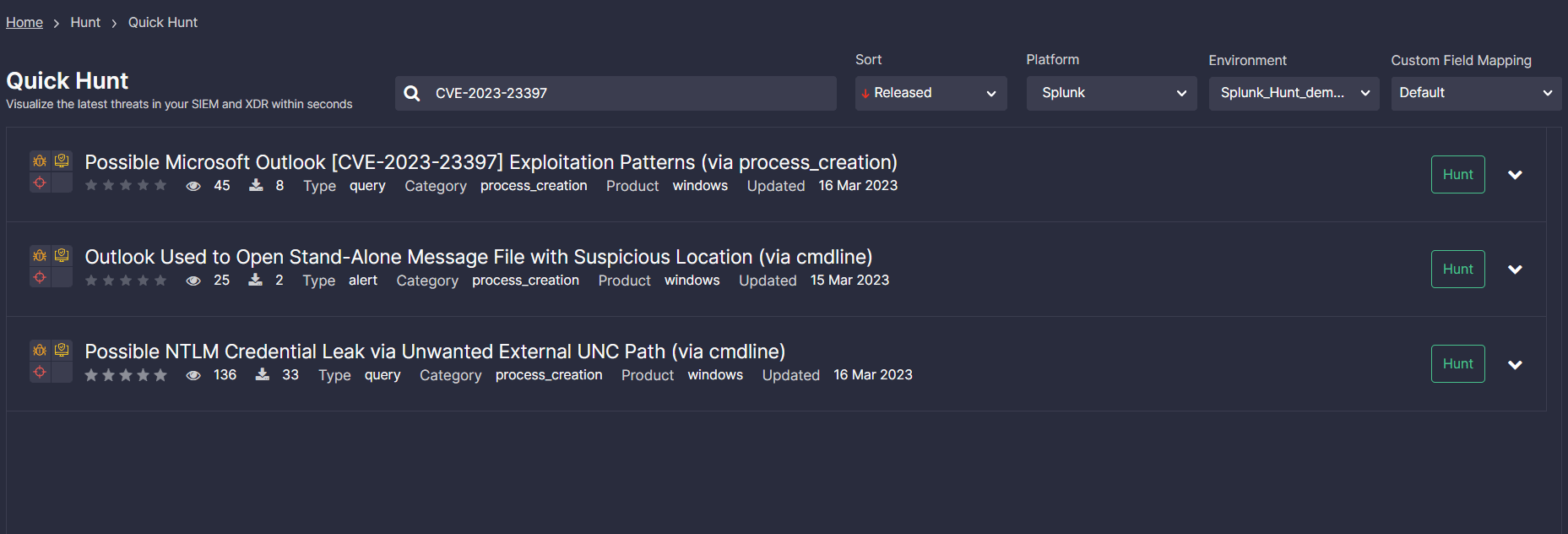
Teams can also make the most of SOC Prime’s Quick Hunt module to search for threats related to the exploitation attempts of CVE-2023-23397. Apply the custom tag “CVE-2023-23397” to filter the list of verified queries based on your current needs, select your platform and environment, and instantly drill down to hunt, shaving seconds off your threat investigation.
Microsoft Outlook Zero-Day Analysis: CVE-2023-23397
March 2023 Patch Tuesday has shed light on a notorious elevation of privilege vulnerability (CVE-2023-23397) impacting all versions of Microsoft Outlook for Windows. The bug enables attackers to grab NTLM creds by sending a malicious email to the victim. According to the advisory by Microsoft, no user interaction is required since the email is triggered automatically when retrieved and processed by the email server.
Despite the fact that NTLM authentication is considered risky, it is still utilized on newer systems to make them compatible with older ones. Authentication, in this case, is performed with password hashes that the server grabs from a client while accessing the shared resource. CVE-2023-23397 enables hackers to steal those hashes, which are further leveraged for successful authentication to the network of interest.
The vulnerability was first discovered by Ukrainian CERT and further investigated by Microsoft’s Incident and Treat Intelligence teams. Microsoft researchers attribute its exploitation attempts to russia-backed threat actors involved in cyber attacks targeting European organizations.
Cybersecurity researchers assume that the malicious activity can be linked to the infamous russian nation-backed hacking collective tracked as APT28 (aka Fancy Bear APT or UAC-0028). Based on the investigation by the State Service of Special Communications and Information Protection of Ukraine (SSSCIP), the APT28 threat actors were behind a series of targeted cyber attacks aimed to cripple Ukraine’s critical infrastructure in early spring 2022. This hacking collective has also been observed in a series of other adversary campaigns against Ukraine in 2022, in which they weaponized the Windows CVE-2022-30190 zero-day vulnerability to spread Cobalt Strike Beacon and various samples of CredoMap malware on the compromised systems.
As potential mitigation measures, cyber defenders recommend timely patching CVE-2023-23397 and applying Microsoft’s script to verify that messages in Exchange use a UNC path and make sure there are no traces of vulnerability exploitation.
Looking for ways to stay ahead of any cyber threats and always have detection for related adversary TTPs at hand? Gain access to over 800 rules for current and emerging CVEs to timely identify the risks and strengthen your cybersecurity posture. Reach 140+ Sigma rules for free or explore the entire list of relevant detection algorithms via On Demand at https://my.socprime.com/pricing/




