Following the disclosure of CVE-2025-4427 and CVE-2025-4428, two Ivanti EPMM vulnerabilities that can be chained for RCE, another critical security issue has emerged, posing a severe threat to organizations that rely on Active Directory (AD). A recently uncovered privilege escalation vulnerability in Windows Server 2025 gives attackers the green light to gain control over any AD user account. The technique, dubbed “BadSuccessor,” abuses the delegated Managed Service Account (dMSA) feature and is easy to exploit under default settings.
Detect BadSuccessor Attacks
The “BadSuccessor” vulnerability poses a serious threat to Active Directory environments due to its potential for widespread disruption. Foundational to identity and access management across businesses of all sizes, AD’s compromise could lead to full domain control by attackers. Specifically, because AD is so deeply embedded in corporate infrastructure, this vulnerability could allow attackers to move laterally, persist undetected, and launch devastating attacks like ransomware.
To spot BadSuccessor attacks on time, register for the SOC Prime Platform, offering a set of relevant detection rules backed by a complete product suite for AI-powered detection engineering, automated threat hunting, and advanced threat detection. Just hit the Explore Detections button below and immediately access the relevant detection stack. Or browse Threat Detection Marketplace using the “badsuccessor” tag.
Security professionals seeking more detection content addressing malicious attacks that pose a threat to Active Directory might apply the Active Directory” tag to review the full collection of detection algorithms.
All rules algorithms can be used across multiple SIEM, EDR, and Data Lake solutions, and are aligned with MITRE ATT&CK® for streamlined threat research. In addition, each vendor-agnostic Sigmac rule is enriched with actionable metadata, such as CTI links, attack timelines, audit configurations, and more cyber threat context.
To streamline threat investigation, security experts might use Uncoder AI – a private IDE & co-pilot for threat-informed detection engineering – now completely free and available without token limits on AI features. Generate detection algorithms from raw threat reports, enable fast IOC sweeps into performance-optimized queries, predict ATT&CK tags, optimize query code with AI tips, and translate it across multiple SIEM, EDR, and Data Lake languages.
In addition, Uncoder AI offers novel functionality inspired by the open-source Attack Flow project by MITRE to help defenders move from isolated behaviors to full adversary sequences. Using Akamai’s report on BadSuccessor, security professionals might turn it into a visual flow, highlighting TTP chains to inform proactive detection logic beyond IOCs. For this purpose, Uncoder AI uses Llama 3.3 customized for detection engineering and threat intelligence processing, hosted at SOC Prime SOC 2 Type II private cloud for maximum security, privacy, and IP protection.
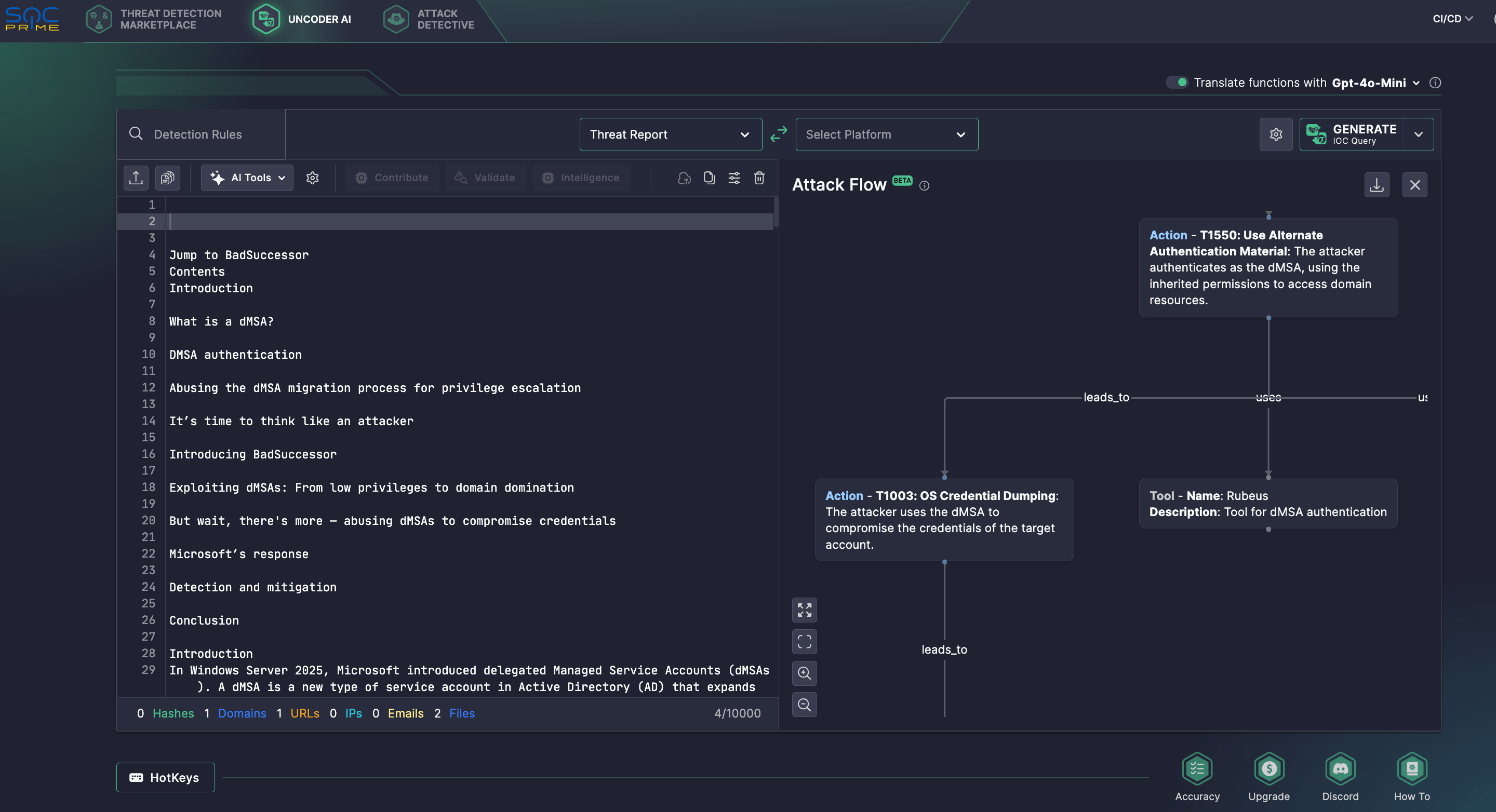
Exploiting BadSuccessor Vulnerability: Attack Analysis
In Windows Server 2025, Microsoft introduced dMSAs, an enhancement to group Managed Service Accounts (gMSAs) designed to simplify the transition from traditional service accounts. Notably, dMSAs enable the seamless “migration” of existing non-managed accounts by marking them as predecessors. However, further investigation revealed a critical privilege escalation path. By exploiting dMSAs, attackers can gain control over any user in the domain, including high-privilege accounts like Domain Admins. The only prerequisite is write access to any dMSA object’s attributes, a permission that is often overlooked in many environments.
Akamai researcher Yuval Gordon has recently uncovered a privilege escalation vulnerability that stems from this newly introduced delegated dMSA feature, which functions under default settings and is easy to exploit. This vulnerability likely impacts the majority of AD-dependent organizations. In 91% of analyzed environments, users outside the domain admins group possessed the necessary permissions to carry out this attack.
There are two primary exploitation scenarios. The first one involves hijacking an existing dMSA to perform the attack, while the other implies creating a new dMSA, a more accessible route, since any user with rights to create msDS-DelegatedManagedServiceAccount objects in a standard Organizational Unit (OU) can do so.
By marking a dMSA as a successor to an existing user, the Key Distribution Center (KDC) assumes a valid migration and automatically transfers the full permissions of the original user to the dMSA, without requiring control over the original account and with no validation or approval mechanisms in place.
This adversary technique, dubbed “BadSuccessor,” effectively gives control of the entire domain to any user who can create or modify a dMSA. It’s a default-enabled vulnerability with severe implications for domain security, particularly because it bypasses traditional administrative barriers.
While Microsoft has acknowledged the issue and intends to address it in the future, no official patch is currently available. In the absence of an immediate fix, organizations are strongly encouraged to restrict the ability to create dMSAs and tighten permissions wherever feasible. To support this, Akamai has released a PowerShell script on GitHub that identifies all non-default users with dMSA creation rights and highlights the OUs where these permissions apply. To minimize the risks of attacks, rely on SOC Prime Platform that curates a complete product suite backed by automation, AI, and real-time threat intel, helping global organizations across diverse industry sectors outscale cyber threats they anticipate most.




