As GenAI continues to shape modern cybersecurity with its powerful advantages for strengthening defense mechanisms, it simultaneously introduces new risks as threat actors increasingly exploit the technology for malicious activities. Adversaries have been recently observed using fake AI installers as lures to spread diverse threats, including the CyberLock and Lucky_Gh0$t ransomware strains and a newly identified malware dubbed “Numero.”
Detect Ransomware and Malware Attacks Using Fake AI Tools
Attackers are increasingly exploiting AI’s rapid adoption to compromise key business assets. Gartner’s 2025 Top Cybersecurity Trends report underscores GenAI’s rising impact, pointing to emerging opportunities for organizations to strengthen their security approaches and adopt more flexible, scalable defense frameworks.
To proactively defend against a new wave of cyber attacks spreading CyberLock, Lucky_Gh0$t, and Numero malicious strains disguised as fake AI tool installers, defenders are encouraged to register for SOC Prime Platform, which provides curated detections and is backed by cutting-edge technologies for strengthening the organization’s cybersecurity posture. Click the Explore Detections button and instantly access Sigma rules to combat relevant threats.
Security experts can also rely on Uncoder AI, which supports detection engineers in their daily detection engineering procedures—from SIEM / MDR / EDR use case development and validation to optimization and documentation—accelerating workflows and improving coverage. Generate detection rules from live threat reports backed by AI, craft detection code with custom AI prompts, validate syntax and refine detection logic across 56+ language formats, and enrich Sigma rules with MITRE ATT&CK (sub-)techniques using your personal AI co-pilot for detection engineering.
As one of Ucoder AI practical use cases, teams can hunt for IOCs related to the Cisco Talos research covering the latest attacks that take advantage of fraudulent AI tool installers. With Uncoder AI, security engineers can instantly parse raw threat intel and convert it into custom hunting queries tailored for the selected SIEM or EDR format.
Uncoder AI also introduces innovative features inspired by MITRE’s open-source Attack Flow project, enabling defenders to shift from analyzing isolated behaviors to mapping complete adversary sequences. By leveraging reports like the one from Cisco Talos, security teams can visualize TTP chains, helping them to develop proactive detection strategies that go beyond traditional IOCs.
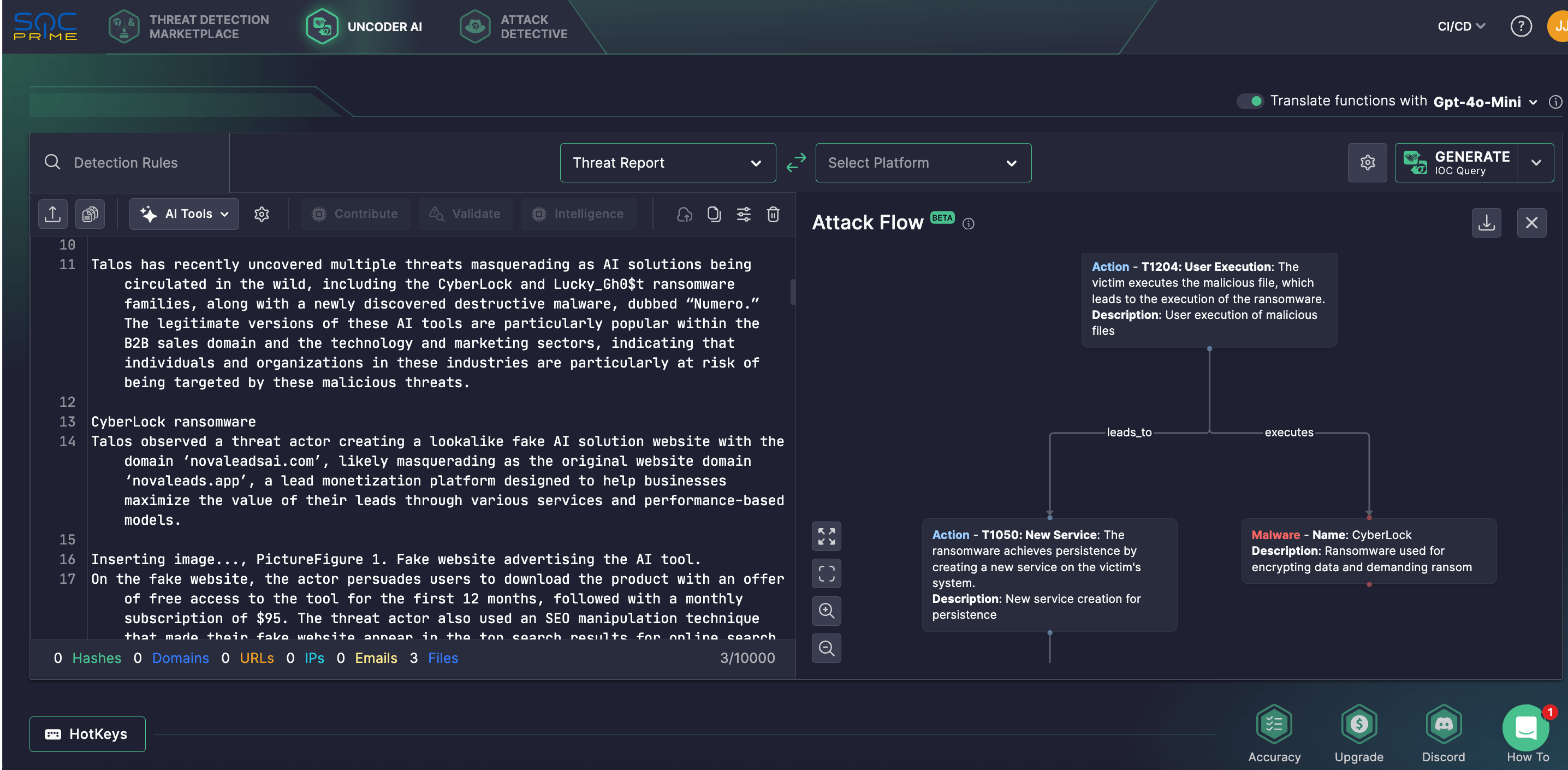
CyberLock, Lucky_Gh0$t Ransomware, and Malware Dubbed Numero: Attack Analysis
Cisco Talos researchers have recently unveiled several emerging threats, including the CyberLock and Lucky_Gh0$t ransomware, along with a newly uncovered malware called “Numero,” which are being distributed under the guise of legitimate AI software installers. Among weaponized AI tools used in these attacks as lures for spreading the infection are widely recognized AI tools like OpenAI ChatGPT and InVideo.
CyberLock ransomware, developed in PowerShell, is designed to encrypt targeted files on a victim’s machine. Another threat, Lucky_Gh0$t, is identified as a variant of Yashma ransomware, a part of the broader Chaos ransomware family, showing only minimal changes to the core binary. In contrast, Numero is classified as destructive malware that disrupts victims by altering Windows GUI components, effectively making infected systems unusable.
Defenders noted that the authentic versions of these AI tools are widely used in B2B sales and marketing, indicating that cybercriminals behind the campaign are likely targeting professionals in those sectors. For instance, one impersonation site, novaleadsai[.]com, is believed to spoof a real lead monetization service called NovaLeads. Researchers suspect it’s being pushed through SEO poisoning to boost visibility in search results artificially. Visitors to the site are enticed with a fraudulent offer: free access to the AI tool for one year, followed by a $95/month subscription. However, the download link delivers a ZIP file containing a .NET executable named NovaLeadsAI.exe, compiled on February 2, 2025, the same day the fake site went live. This executable acts as a dropper that launches the PowerShell-based CyberLock ransomware.
CyberLock ransomware is delivered via a .NET loader. Upon execution, it hides the PowerShell window using Windows API calls and decrypts an embedded public key to derive AES keys for file encryption. If not already running with admin rights, it attempts to elevate privileges and relaunch itself. After encrypting the targeted files, CyberLock drops a ransom note named ReadMeNow.txt on the desktop and sets the desktop wallpaper to an image downloaded from a cybersecurity blog. It then uses the built-in Windows tool cipher.exe with the /w flag to overwrite free space on the hard drive, making deleted files unrecoverable and complicating forensic analysis. While this wiping technique has been seen in previous APT attacks, Talos found no link to earlier campaigns.
Researchers observed that adversaries have been spreading Lucky_Gh0$t ransomware via a fake installer posing as a premium version of ChatGPT. The malicious self-extracting (SFX) archive included a folder containing the ransomware payload named “dwn.exe”, mimicking Microsoft’s legitimate “dwm.exe”. The package also bundled legitimate Microsoft open-source AI tools from their official GitHub repository, typically used in Azure-based AI development. If a victim executes the SFX installer, the embedded script triggers the ransomware. Lucky_Gh0$t, a variant of Yashma ransomware, encrypts files smaller than 1.2GB and removes volume shadow copies and backups to hinder recovery. The ransom note left at the conclusion of the attack contained a unique decryption ID and directed victims to contact the attackers through the Session messaging app to negotiate payment and receive a decryptor.
Another malicious sample used in these attacks, leveraging fraudulent AI installers, is the use of a new destructive malware called “Numero,” masquerading as an installer for the legitimate AI video tool InVideo AI. The fake installer, embedded with a malicious batch file, VBScript, and the Numero executable (“wintitle.exe”), drops its payload into the user’s temp folder and launches it in an infinite loop. Once executed, the batch file runs Numero and pauses for 60 seconds using VBScript. Written in C++ and compiled in January 2025, Numero behaves like window manipulation malware. It evades detection by checking for known analysis tools and debuggers, then repeatedly corrupts the victim’s desktop by overwriting GUI elements with the string “1234567890,” rendering the system unusable. The malware keeps restarting through the batch loop, ensuring persistence.
The overlap between AI’s growing influence and the adversary’s use of fake installers highlights the pressing importance of strong cybersecurity defenses to counter these evolving threats. Defenders recommend validating the legitimacy of AI software sources and downloading only from trusted vendors to minimize the risk of infections. By leveraging SOC Prime Platform, backed by ethical and responsible AI, automation, real-time threat intel, and built on zero-trust principles, global organizations can equip their security teams with future-proof technologies for proactive defense and seamlessly navigate the ever-expanding attack surface.




