Threat actors often exploit cloud services for C2 to disguise their actions as normal, legitimate traffic. The nefarious Chinese state-backed APT41 hacking collective has been observed employing the TOUGHPROGRESS malicious strain delivered through a hacked government website and targeting multiple other governmental entities. What sets this attack apart is that the malware uses Google Calendar for C2 operations.
Detect APT41 Attacks
Amid rising geopolitical tensions, the threat from Advanced Persistent Threats (APTs) has intensified, with state-sponsored actors increasingly targeting critical infrastructure, financial systems, and government networks using zero-day exploits, spearphishing, and advanced malware.
According to the 2025 CyberThreat report by Trellix, China remains a dominant force in the APT landscape. APT40 and Mustang Panda were the most active groups, responsible for 46% of observed activity, while APT41’s operations surged by 113% in Q1, underscoring the evolving scale and persistence of campaigns, such as the latest Google Calendar misuse for malware distribution.
Register to the SOC Prime Platform and access a broad collection of Sigma rules addressing the latest APT41 campaign, backed by a complete product suite for AI-powered detection engineering, automated threat hunting, and advanced threat detection. Just press the Explore Detections button below and immediately drill down to a relevant detection stack compatible with multiple SIEM, EDR, and Data Lake solutions, aligned with MITRE ATT&CK, and enriched with actionable CTI.
Cyber defenders looking for more content addressing TTPs used by China-backed APT41 might browse Threat Detection Marketplace using “APT41” tag or explore a broader collection against nation-state actors by applying “APT” tag in search.
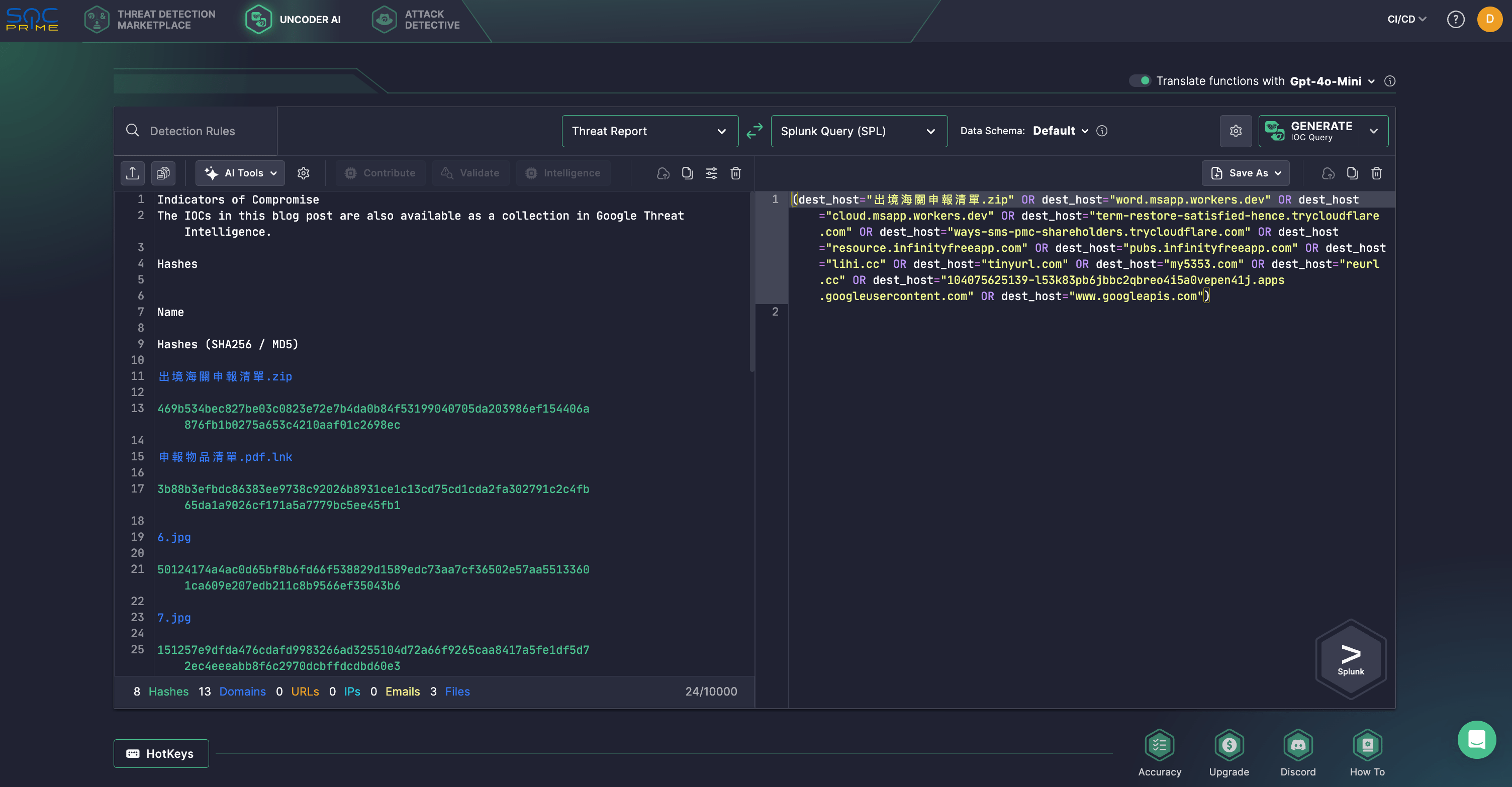
To streamline threat investigation, security experts might use Uncoder AI – a private IDE & co-pilot for threat-informed detection engineering – now available without token limits on AI features. Generate detection algorithms from raw threat reports, enable fast IOC sweeps into performance-optimized queries, predict ATT&CK tags, optimize query code with AI tips, and translate it across multiple SIEM, EDR, and Data Lake languages.
For instance, security professionals can hunt for IOCs from the Google Threat Intelligence Group report on the latest APT41 campaign. With Uncoder AI, security experts can effortlessly parse these IOCs and transform them into custom queries tailored for the chosen SIEM or EDR platform.
APT41 Attack Analysis
Defenders have uncovered a new cyber-espionage campaign by a China-based state-sponsored threat group that weaponized Google Calendar to target government organizations. In a recent report, Google researchers attributed the activity to APT41 (aka Bronze Atlas, BARIUM, Earth Baku, Brass Typhoon, HOODOO, Wicked Panda, or RedGolf), a long-standing, nation-backed hacking group known for targeting foreign governments and industries such as logistics, media, automotive, and technology.
The campaign, detected in late October by Google, began with spearphishing emails that led victims to a weaponized ZIP file containing malware hosted on a compromised government website. The archive contains a folder and a Windows shortcut (LNK) disguised as a PDF file. Inside the folder are what seem to be seven images of arthropods, labeled “1.jpg” through “7.jpg.” The infection chain starts when the victim opens the shortcut file, which displays a decoy PDF claiming the listed species must be declared for export. Notably, the files labeled “6.jpg” and “7.jpg” are not actual images but are instead used as part of the deception. Upon execution, the file launches a covert malware called ToughProgress.
The malware consists of three sequential modules, each serving a specific purpose and incorporating various stealth and evasion methods such as in-memory execution, encryption, compression, process hollowing, control flow obfuscation, and the use of Google Calendar for C2. The three malicious modules include PLUSDROP, a DLL component responsible for decrypting and loading the next stage directly into memory, PLUSINJECT, which carries out process hollowing by injecting the final payload into a legitimate svchost.exe process, and TOUGHPROGRESS used to run malicious activities on infected Windows machines and communicate with the attacker through Google Calendar.
What sets ToughProgress apart is its innovative use of Google Calendar as a C2 mechanism. The malware interacts with an attacker-controlled Google Calendar by creating and modifying events to facilitate data exchange. Once installed, ToughProgress creates a calendar event dated May 30, 2023, embedding encrypted, exfiltrated data within the event description.
Encrypted commands are embedded by the attackers into Calendar events dated July 30 and 31, 2023. The malware checks these events, decrypts and executes the commands on the infected Windows machine, and then uploads the execution results into a new Calendar event, allowing cybercriminals to retrieve the output remotely.
As potential APT41 mitigation measures aimed at minimizing the risks of the TOUGHPROGRESS intrusions, Google developed custom fingerprints to detect and remove malicious Google Calendar instances and terminate attacker-controlled Workspace projects. Harmful domains and files were also added to Safe Browsing blocklists. In collaboration with Mandiant, the vendor notified affected organizations, providing threat intel and TOUGHPROGRESS traffic samples to support incident response.
As Chinese state-sponsored APT groups, like APT41, ramp up cyber-espionage attacks, often targeting government entities and employing advanced stealth and evasion tactics, defenders are increasingly seeking smarter strategies to counter these evolving threats. SOC Prime curates a complete product suite for enterprise security backed by AI, automation, and actionable threat intel to help organizations outscale attacks of increasing complexity and sophistication.




