Just over a month after the disclosure of a critical Confluence zero-day tracked as CVE-2023-22515, a novel vulnerability emerges in the cyber threat arena impacting Atlassian products. Adversaries are setting eyes on a recently fixed and maximum severity vulnerability known as CVE-2023-22518 in all versions of Confluence Data Center and Confluence Server, which enables them to bypass authentication. Attackers abuse the CVE-2023-22518 exploit to encrypt the files of targeted users with Cerber ransomware.
Detect CVE-2023-22518 Exploitation Attempts
Another day, another critical security bug on the radar. In view that CVE-2023-22518 obtained a high severity rating and impacts all Confluence versions, cyber defenders require a reliable source of detection content to stop the avalanche of in-the-wild attacks relying on the security issue in the limelight.
SOC Prime Platform for collective cyber defense offers a set of curated Sigma rules tailored for dozens of security analytics platforms and mapped to the MITRE ATT&CK® framework for streamlined threat investigation.
To identify possible exploitation attempts in Windows/Linux environments, leverage the dedicated pieces of content below.
Possible CVE-2023-22518 (Atlassian Confluence) Exploitation Attempt [Windows] (via process_creation)
Possible CVE-2023-22518 (Atlassian Confluence) Exploitation Attempt [Linux] (via process_creation)
Possible CVE-2023-22518 (Atlassian Confluence) Exploitation Attempt (via webserver)
Notably, the last rule in the list (devoted to CVE-2022-26134 exploit detection and released in 2022) helps to spot offensive activity related to CVE-2023-22518 due to significant overlaps in behavior for the Linux environment.
Also, the rule below allows the detection of generic malicious patterns related to CVE-2023-26134 exploitation on Windows instances:
Possible Web Server or WebApp Exploitation (via cmdline)
To investigate the post-exploitation activity in Windows and Linux environments related to recent attacks, check out Sigma rules below:
Remote File Copy via Standard Tools (via cmdline)
Download or Upload via Powershell (via cmdline)
Reach a comprehensive list of SOC content aimed at emerging CVEs detection by clicking the Explore Detections button. Security professionals can obtain in-depth intelligence accompanied by ATT&CK references and CTI links, as well as get actionable metadata tailored to their organization-specific needs for streamlined threat research.
CVE-2023-22518 Analysis
Atlassian has recently released a security notice warning defenders of a novel improper authorization vulnerability identified as CVE-2023-22518 that impacts all Confluence versions of Data Center and Server software. On November 6, 2023, Atlassian added the updates highlighting the active exploitation of CVE-2023-22518 and its use in ransomware attacks. Due to the dramatically increasing risks associated with the uncovered security bug and the PoC exploit publicly available, CVE-2023-22518 has received the highest critical rating reaching 10 on the CVSS scale. Luckily, the vulnerability has no impact on Atlassian Cloud websites reached through the atlassian.net domain.
The uncovered security bug enables an unauthenticated attacker to reset Confluence and generate an account with elevated privileges for performing all administrative actions, which can lead to a full system compromise.
Rapid7 recently observed the exploitation of CVE-2023-22518 in a set of customer environments, including attempts to deploy Cerber ransomware on vulnerable Confluence servers.
With all Confluence Data Center and Server versions being impacted, Atlassian recommends instantly applying the patch to the designated LTS version or a more recent one to mitigate the threat. In case you have issues applying the patch, backing up your potentially impacted instance, restricting it from external network access, and disabling access on the specific Confluence endpoints can be used as interim remedies to reduce attack vectors.
Based on a brief Shodan search, roughly 20K+ Confluence instances are currently exposed on the internet, however, it’s hard to specify how many of them are vulnerable to CVE-2023-22518 attacks. This number has significantly risen since the disclosure of another Confluence vulnerability tracked as CVE-2022-26134 in 2022.
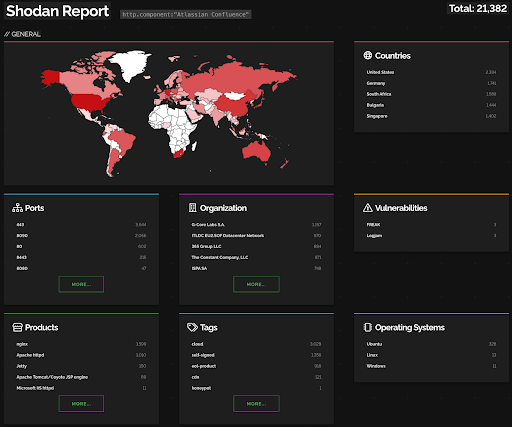
The growing risks of the CVE-2023-22518 exploitation attempts due to the PoC discovery require ultra-responsiveness from defenders to safeguard the organization’s infrastructure. SOС Prime’s Threat Detection Marketplace empowers cyber defenders with access to the latest behavior-based detection algorithms enriched with tailored intelligence to stay ahead of ransomware attacks and emerging threats of any scope.




