Introduction
COVID-19 / Coronavirus phishing is on the uptick and will likely remain a primary theme/lure for many months to come. This blog post makes recommendations as far as COVID-19 specific phishing and other threats brought on by increased teleworking.
Has The Threat of Phishing Changed?
Has the Threat Changed? Kind of. There is a great sense of urgency surrounding COVID-19 / Coronavirus. This urgency increases the likelihood the average person falls victim to phishing. Attackers know this and therefore we expect and are observing an increase in targeting using COVID-19 and Coronavirus themes/lures. Additional themes/lures will likely also increase in usage and effectiveness against victims surrounding telework.
However, as far as the techniques and tactics in use by adversaries in phishing attacks, things are largely the same.
In this blog post we will cover some aspects of phishing, what we expect to see regarding coronavirus, and how you can protect your organization against the threats.
Types of Phishing
Generally, there are three primary goals of phishing attacks.
- Deliver Malware
- Link to malware
- Attach malware to email
- Ransomware, Banking Trojans, Web Skimming, Espionage, etc
- Obtain Sensitive Information
- Typically organizations are most concerned with username / password
- Typically link to fake login page
- Fraud / Scams
- Convince victim to send resources (money and even equipment) via
- Fake Invoices
- Fake Purchase Orders
- Fake Charity
- Convince victim to send resources (money and even equipment) via
Phishing Themes Lures
Criminals take advantage of a sense of urgency to trick their victims into executing malware on their endpoints, send money/supplies to fake charities, or to reveal sensitive information (username and password). SOC Prime expects to observe an increase of COVID-19 / Coronavirus and related themes/lures such as:
- COVID-19 / Coronavirus – Information
-
-
- A criminal poses as an authority delivering a document or a link to a document containing important information regarding COVID-19 / Coronavirus.
-
- COVID-19 / Coronavirus – Scare Emails
-
-
- A criminal poses as an authority providing “urgent information” regarding COVID-19 / Coronavirus or event attempts at extorting victims with the threat of viral infection
-
- COVID-19 / Coronavirus – Test / Cure
-
-
- A criminal poses as having a test or cure for COVID-19
-
- Economic Relief
-
-
- A criminal poses as the government, employer, or charity offering economic relief
-
- VPN / Teleconference / VDI Client Deployment / Update
-
-
- A criminal poses as an Information Technology department with an update or deployment of software that the company uses / will use to increase their telework capabilities.
-
- Purchase Order / Invoice Scams for COVID-19 related medical supplies (PPE, ventilators, respirators, medicine)
-
-
- A criminal sends fake purchase orders or invoices for COVID-19 related supplies.
-
- Travel Related Scams
-
- A criminal poses as an employee/friend/relative stuck in a foreign country
- A criminal poses as an airline / hotel with an ‘update’ regarding future travel plans
Phishing Lures Containing Malware / Ransomware
For the average organization, ransomware is currently their largest threat. Ransomware delivered through phishing often takes advantage of documents / file types that contain code (script files, office documents). Exploits are still a common threat, but are expensive, more difficult to implement, and normally not necessary.
Common First Stages used in Phishing
- Use of links to malicious files has increased substantially to bypass email filtering / sandboxing (T1192)
- Use of encrypted compressed archives (.zip, .7z, .iso, .tar, etc) to bypass scanning & sandboxes (T1140)
- Microsoft Office Documents (especially xlsx, xlsm, xls, doc, docm, docx)
- Rich Text File Documents T1193
- PDF Documents T1193
- Scripts / Dynamic Content embedded in files or attached directly (.vbs, .vbe, .js, .jse, .wsh, .cmd, .bat, .ps1, .wsh, .wsc, .hta, .pif, .lnk, .com, .reg) T1193
- For instance a .vbs file can be embedded in a PDF, Word document, Zip file, etc.
- Executables (.exe, .scr, and those that rely on third party software like jar)
Post Compromise
Not all is lost once an endpoint is compromised as phishing as an attack does not sit in a silo. In order to obtain their objective criminals normally must escalate their privileges locally, then on the domain, and also move laterally to critical assets.
Typically, execution occurs almost instantly post “initial access”. Normally, this involves direct process creation via powershell, cscript, wscript, mshta, rundll32, or other techniques. Sneakier techniques such as parent-child process chain breaking (via PPID spoofing / COM) and process injection are also becoming more common.
Regardless, In a typical attack chain there is plenty to alert on.
Specifically, SOC Prime has identified the following techniques as being most common in recent phishing attacks.
- T1192 (Spearphishing Link)
- T1193 (Spearphishing Attachment)
- T1059 (Command-Line Interface)
- T1086 (PowerShell)
- T1085 (Rundll32)
- T1218 (Signed Binary Proxy Execution)
- T1053 (Scheduled Task)
- T1050 (New Service)
Content to the Rescue
At SOC Prime we are super fans of SIGMA. Our threat bounty developers as well as the SOC Prime team has released a lot of relevant content (much for free) that covers most of the ATT&CK Framework techniques. Content that generally focuses on behaviors over TTPs. That means this content works regardless of the phishing theme or lure. So, if you install this content it will be able to help you during the next crisis being used in phishing lures.
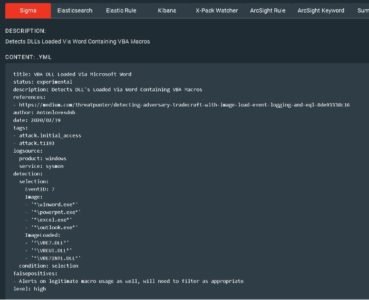
For instance, the rule “VBA DLL Loaded via Microsoft Word” will detect instances of office loading documents containing macros. The most commonly abused file type to deliver phishing contents.
We have tagged this content and more in the Threat Detection Marketplace (TDM) with “covid19_ttp”
https://tdm.socprime.com/?ruleMaster=true&searchValue=covid19_ttp
Additional Measures for Hardening your Organization Against Phishing
This list is not comprehensive. However, these are some effect methods that will help protect your organization against most first stage malware attacks. If you haven’t taken one of the steps below, you should identify its impact to your organization and then test and deploy the changes that are possible.
- User Awareness
- Ensure Anti-Virus definitions are updated regularly
- Limit administrative access
- Make use of application whitelisting
- Change default file associations for commonly abused file types to not-execute
- Common for .vbs, .vbe, .js, .jse, .bat, etc to be changed from their current file association to “notepad.exe” on endpoints. This way if a user falls for a phish the document is opened by notepad instead of executed. https://support.microsoft.com/en-us/help/4028161/windows-10-change-default-programs
- Use of multi-stage / multi-factor authentication
- Non-sms / non-email based multifactor is optimal
- Install 7zip/Winrar and other third party compression utilities only for users who require it.
- Disable office macros
- Block SMB traffic destined outside of your organization
- Use VPN software that keeps users from accessing the internet unless they are VPN’d in.