Since at least 2022, the hacking collective tracked as UAC-0024 has been launching a series of offensive operations targeting Ukraine’s defense forces. The group’s cyber-espionage activity mainly focuses on intelligence gathering leveraging CAPIBAR malware. Based on attacker TTPs along with the uncovered use of another malware dubbed Kazuar, the adversary activity can be linked to the nefarious Turla APT group backed by the russian Federal Security Services.
Turla APT aka UAC-0024 Attack Description
CERT-UA researchers recently issued a heads-up covering an overview of the ongoing cyber-espionage operations by UAC-0024 hackers or Turla APT. The russia-linked group, which in May 2023 was observed to be behind a long-term campaign against NATO countries, is also known under the monikers Iron Hunter, Krypton, or Secret Blizzard, and alternatively tracked by CERT-UA as UAC-0003, largely leverages the phishing attack vector with the public sector, diplomatic, and military organizations being its primary targets.
For more than a year, the infamous russia-backed hacking gang has been launching targeted cyber-espionage attacks against Ukraine and its allies abusing the CAPIBAR malware also tracked as DeliveryCheck or GAMEDAY. This malicious strain applies the XSLT language and COM-hijacking and can be installed on the compromised MS Exchange server disguised as a MOF file via a specific PowerShell utility, which enables adversaries to turn a legitimate server into a tool for remote malware management.
At the initial attack stage, UAC-0024 hackers massively distribute emails that contain attachments with a file and macro luring potential victims into opening them. Opening a legitimate macro, which includes a set of code snippets that launch PowerShell, triggers an infection chain on the targeted systems. This enables hackers to drop the KAZUAR backdoor, which is capable of performing dozens of malicious functions, including launching JavaScript code via ChakraCore, collecting event logs from the OS registry, credential theft (like stealing user passwords, cookies, bookmarks, and other sensitive data) or stealing databases and software configuration files. Also, threat actors can exploit the Rclone open-source file-management command-line utility to exfiltrate data from compromised computers.
Detect UAC-0024 Attacks Against Ukraine Covered in the CERT-UA#6981 Alert
The persistent attacks by russia-affiliated threat actors tracked as Turla APT or UAC-0024 have been in the limelight in the cyber threat arena for more than a year, capturing the full attention of cyber defenders. Progressive organizations striving to implement proactive cyber defense against emerging russia-backed threats can leverage thousands of relevant Sigma rules, including a curated content stack for UAC-0024 attack detection.
By clicking the Explore Detections button, teams can reach the entire collection of dedicated Sigma rules tagged “CERT-UA#6981”, “UAC-0024”, or “UAC-0003” according to the relevant CERT-UA notice and corresponding group identifiers. The detection rules and hunting queries are applicable to dozens of security analytics platforms and data lake solutions, enhanced with tailored intelligence, and are ready to deploy in your environment.
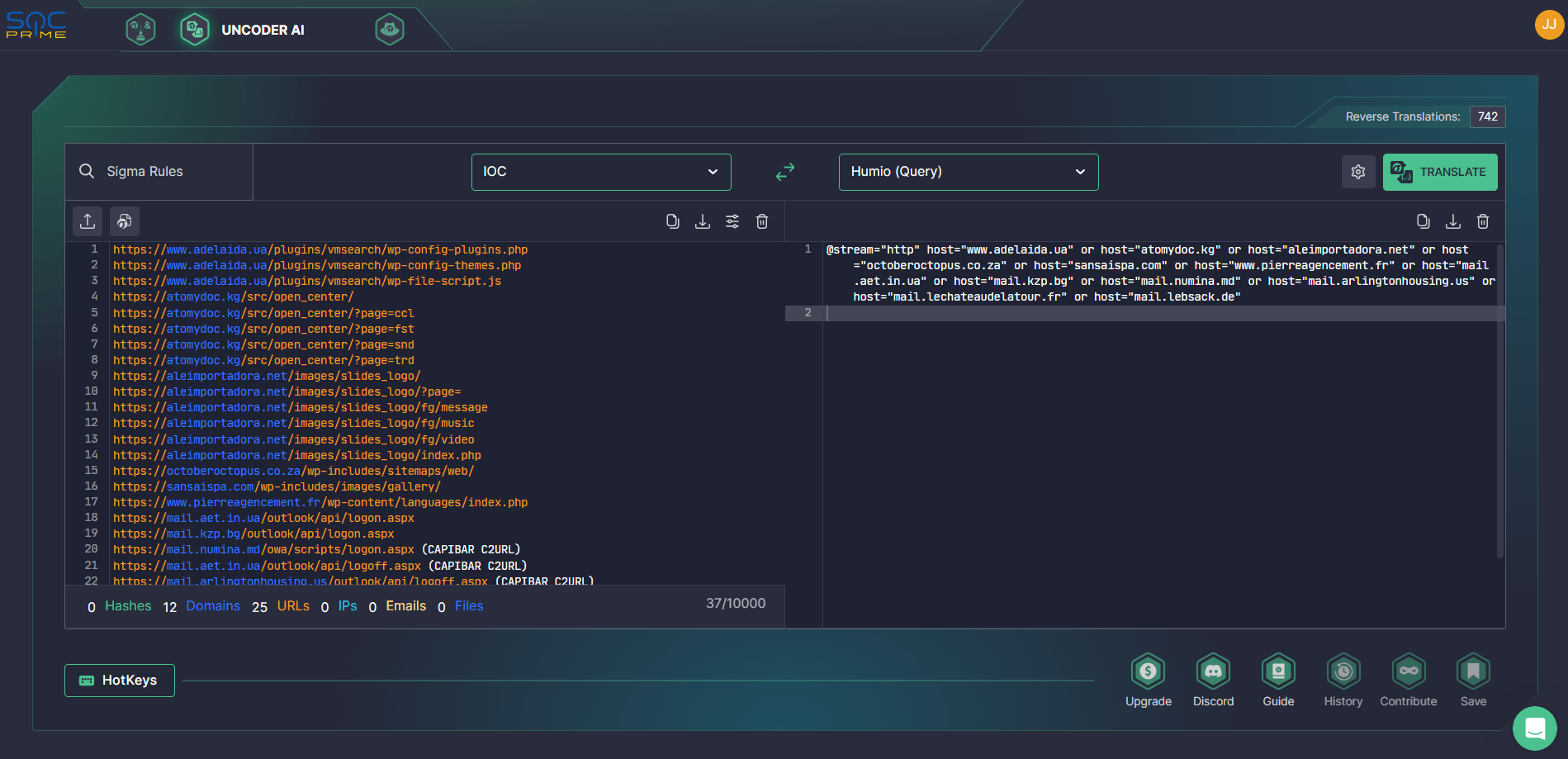
CERT-UA also provides a list of relevant file and host indicators of compromise in the CERT-UA#6981 alert enabling security engineers to effectively hunt for Turla-related threats. Backed by SOC Prime’s Uncoder AI, hunting for IOCs with instantly generated IOC queries customized to your security needs can help shave seconds off threat investigation.
MITRE ATT&CK® Context
All the above-referenced Sigma rules for UAC-0024 attack detection are aligned with the MITRE ATT&CK framework v12 addressing the corresponding tactics and techniques. Explore the table below to gain insights into the in-depth cyber threat context behind related russia-linked cyber-espionage operations and timely remediate threats of any scale:
Tactics | Techniques | Sigma Rule |
Defense Evasion | Obfuscated Files or Information (T1027) | |
Execution | Command and Scripting Interpreter (T1059) | |
Scheduled Task/Job (T1053) | ||
Command and Control | Ingress Tool Transfer (T1105) | |
Exfiltration | Exfiltration Over Web Service (T1567) | |
Persistence | Event Triggered Execution (T1546) |




