China-linked cyber-espionage operations are rapidly escalating, with state-sponsored activity up 150% and targeted attacks on financial, media, manufacturing, and industrial sectors rising by as much as 300% according to CrowdStrike’s 2025 Global Threat Report. Recently, defenders identified the BRICKSTORM backdoor being used to maintain long-term persistence in U.S. organizations across multiple sectors, including legal and tech firms. The campaign, attributed to APT UNC5221 and related China-nexus clusters, enabled undetected access to victim networks for over a year.
Detect BRICKSTORM Malware
Amid rising geopolitical tensions, the threat posed by APTs is intensifying. State-sponsored actors are increasingly targeting critical infrastructure, financial systems, and government networks through zero-day exploits, spearphishing, and advanced malware.
China continues to dominate the APT landscape, with groups from China, North Korea, Iran, and Russia showcasing growing sophistication and adaptability throughout 2024, according to the CyberThreat report by Trellix. These actors remain among the most active globally, using cyber operations to advance their geopolitical objectives. Cyber-espionage has become a central focus, with campaigns becoming more targeted, covert, and technically advanced.
The recently uncovered BRICKSTORM malware campaign exemplifies this evolution, leveraging a highly sophisticated, multi-stage approach to infiltrate organizations in the legal sector. Its techniques highlight the increasing precision of modern espionage operations and the urgent need for defenders to anticipate and counter these threats.
Register for the SOC Prime Platform and access the latest CTI & curated Sigma rules addressing the BRICKSTORM malware attacks. Just press the Explore Detections button below and immediately drill down to a relevant detection stack compatible with multiple SIEM, EDR, and Data Lake solutions, aligned with MITRE ATT&CK, and enriched with actionable CTI.
Cyber defenders looking to track content updates on BRICKSTORM malware detection might browse Threat Detection Marketplace using the “Brickstorm” tag, or the “APT” tag in search to explore a broader collection against nation-state actors.
To streamline threat investigation, security experts might use Uncoder AI, an IDE and co-pilot for detection engineering, which is now enhanced with a new AI Chat Bot mode and the MCP tools support. With Uncoder, defenders can instantly convert IOCs into custom hunting queries, craft detection code from raw threat reports, generate Attack Flow diagrams, enable ATT&CK tags prediction, leverage AI-driven query optimization, and translate detection content across multiple platforms. For instance, security professionals can visualize Attack Flow using the Madinat & Google Threat Intelligence Group report on the BRICKSTORM malware.
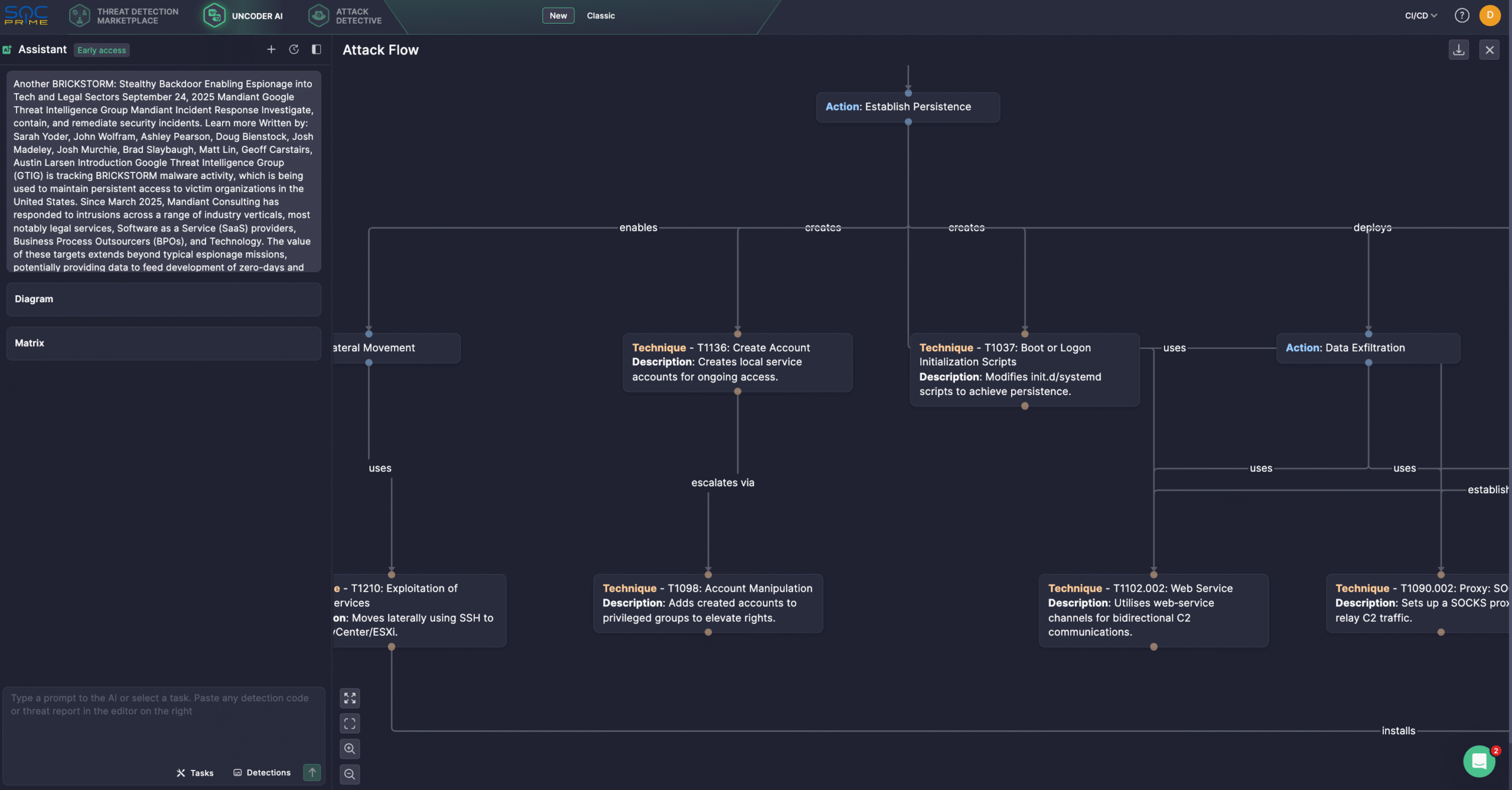
BRICKSTORM Malware Analysis
Google researchers warn that China-linked actors have been deploying the Go-based BRICKSTORM backdoor to spy on U.S. tech, legal, SaaS, and BPO organizations, stealing data undetected for over a year. The campaign has been active since March 2025 and is attributed by Mandiant to APT UNC5221, a China-nexus group known for leveraging zero-days in espionage operations.
While UNC5221 has sometimes been linked to Silk Typhoon, defenders currently treat them as distinct clusters. The group focuses on long-term, stealthy access by deploying backdoors on appliances that lack traditional EDR support, using lateral movement and data theft techniques that generate little to no telemetry. Modifications to the Go-based BRICKSTORM backdoor, which is equipped with SOCKS proxy functionality and cross-platform support, have allowed adversaries to remain under the radar in victim environments for over a year.
Researchers have observed BRICKSTORM on Linux and BSD-based appliances from multiple vendors, consistently targeting VMware vCenter and ESXi hosts. In several cases, BRICKSTORM was deployed to network appliances before pivoting to VMware systems using valid, likely stolen, credentials. Notably, attackers even installed BRICKSTORM on a vCenter server after the incident response had begun, highlighting their adaptability.
In at least one intrusion, UNC5221 exploited a zero-day vulnerability; in others, post-exploitation scripts with anti-forensic capabilities obscured entry points. BRICKSTORM samples are often disguised to mimic legitimate processes, and C2 infrastructure has leveraged Cloudflare Workers, Heroku apps, and dynamic DNS services like sslip.io or nip.io. No C2 domains have been reused across victims, emphasizing the group’s focus on operational security.
In one case, attackers compromised a vCenter server by installing a malicious Java Servlet filter on the Apache Tomcat web interface. Using a custom in-memory dropper, they bypassed the need for configuration changes or restarts. The filter, dubbed BRICKSTEAL, intercepted HTTP login requests by decoding credentials from HTTP Basic authentication, often Active Directory accounts with high privileges.
In one incident, the attacker leveraged valid administrator credentials to move laterally into a system running Delinea (formerly Thycotic) Secret Server, where forensic evidence indicated the use of a tool, such as a secret stealer, to automatically extract and decrypt stored credentials.
BRICKSTORM typically served as the primary backdoor for hands-on activity, with additional compromised appliances acting as backups. To deploy it, adversaries often connected over SSH using legitimate credentials. In some cases, these were retrieved from a previously accessed password vault or uncovered in a PowerShell script. Attackers were also observed enabling SSH via the ESXi web UI or VAMI before installing BRICKSTORM.
Asversaries also used valid credentials for lateral movement into VMware environments, maintaining persistence by altering init.d, rc.local, or systemd files so the backdoor launched automatically on reboot. In other cases, they deployed a JSP web shell, tracked as SLAYSTYLE (aka BEEFLUSH), to execute arbitrary OS commands via HTTP requests.
Investigations display adversaries often targeted the emails of key personnel, using Microsoft Entra ID Enterprise Applications with mail.read or full_access_as_app scopes to access any mailbox. Targets included developers, admins, and individuals tied to PRC economic or espionage priorities.
For data theft, UNC5221 used BRICKSTORM’s SOCKS proxy to tunnel into victim systems, logging into internal code repositories with stolen credentials to download archives or directly browsing files via UNC paths. In some intrusions, BRICKSTORM was later removed, but forensic analysis of backups revealed its prior presence.The BRICKSTORM campaign is a highly sophisticated operation that evades advanced security defenses and targets high-value organizations. UNC5221’s access allows them to move into customers of compromised SaaS providers or exploit zero-day vulnerabilities in enterprise systems, underscoring the need for rapid and proactive response from defenders. By leveraging SOC Prime’s complete product suite backed by top cybersecurity expertise, AI, automated capabilities, and real-time threat intelligence, organizations can proactively defend against APT attacks and other critical threats they anticipate most.




