The latest advisory issued by law enforcement agencies within Australia, the U.S., Canada, Germany, the U.K., New Zealand, South Korea, and Japan, warns of the growing threat posed by APT40 operated on behalf of Beijing’s Ministry of State Security (MSS). Specifically, the advisory details the activities of the People’s Republic of China state-sponsored group able to swiftly adapt and deploy proof-of-concent (PoC) exploits for new vulns, promptly leveraging them to monitor networks of interest and target unpatched systems.
Detect APT40 Attacks Leveraging Newly Discovered Vulnerabilities
In Q1 2024, APT groups from various regions including China, North Korea, Iran, and russia exhibited significantly enhanced and inventive offensive techniques, posing serious challenges to the global cybersecurity environment. As geopolitical tensions drastically escalate during recent years, APT threat becomes one of the major menaces for cyber-defenders.
The latest joint advisory by cybersecurity agencies warns of the growing threat from China-backed APT40 group accused of targeting multiple government and business networks worldwide, with specific interest in the private & public sector of Australia and the U.S. To proactively identify and withstand potential attacks, cyber defenders require advanced threat detection & hunting tools.
SOC Prime Platform for collective cyber defense aims to equip every security team with the best solutions and curated detection content for the latest threats released under 24-hour SLA. To stay on top of APT40 attacks, security professionals can leverage a set of detection rules addressing TTPs described in AA24-190A advisory by CISA.
Just tap the Explore Detections button below and immediately drill down to a curated list of Sigma rules associated with the latest APT40 campaigns analyzed by CISA. All the rules are compatible with 30+ SIEM, EDR, and Data Lake platforms and mapped to the MITRE ATT&CK framework. Additionally all the rules are enriched with extensive metadata, threat intelligence details, attack timelines, and triage recommendations to smooth out threat investigation.
As APT40 hackers tend to exploit exposed public-facing infrastructure over TTPs relying on user interaction, adapting PoC exploits for the latest CVE is one of the most frequently used ways to gain the initial foothold on the network of interest. Check out the list below to learn about the prominent CVEs weaponized by the Chinese APT actor accompanied by relevant detection rules:
Log4J
Detection Rules for CVE-2021-44228
Atlassian Confluence Vulnerabilities
Detection Rules for CVE-2021-31207
Detection Rules for CVE-2021-26084
Microsoft Exchange Vulnerabilities
Detection Rules for CVE-2021-31207
Detection Rules for CVE-2021-34523
Detection Rules for CVE-2021-34473
Cybersecurity experts seeking additional detection content to analyze APT40’s activities retrospectively and stay on top of TTPs leveraged by the group can explore a dedicated rule set curated by the SOC Prime Team. Just browse Threat Detection Marketplace using the “APT40” tag or use this link to access the APT40 rule collection directly.
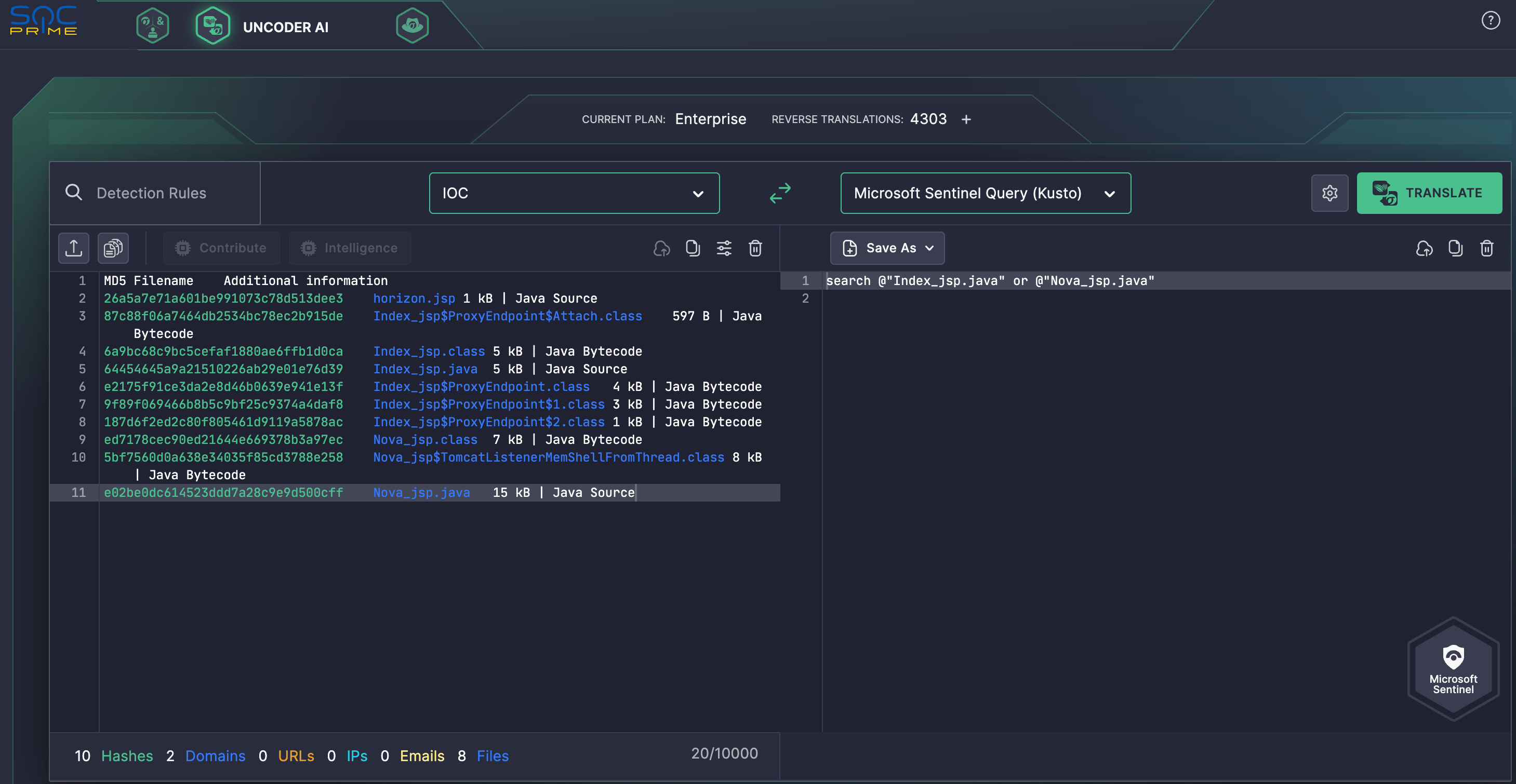
To simplify the search for the file, host, or network IOCs mentioned in the AA24-190A advisory by CISA, security engineers can take advantage of the SOC Prime’s Uncoder AI with its built-in IOC packager. It enables automated conversion of CTI details into custom IOC queries that are instantly compatible with your preferred SIEM or EDR format.
As Chinese state-sponsored actors are currently one of the most active hacking collective on the global arena, organizations might be also interested in a broader detection stack addressing tactics, techniques, and procedures most relevant to PRC-affiliated actors.
APT40 Attacks Analysis
The latest joint cybersecurity advisory, led by Australian Cyber Security Centre (ACSC) shed light on the activity of the People’s Republic of China (PRC) nation-state group tracked as APT40. The adversary collective, also referred to as Bronze Mohawk, Gingham Typhoon (formerly Gadolinium), ISLANDDREAMS, Kryptonite Panda, Leviathan, Red Ladon, TA423, and TEMP.Periscope, has been active since at least 2013, conducting cyber attacks on entities in the Asia-Pacific region.
Back in 2022, the ACSC became aware of an APT40 attack on an undisclosed local organization. With the victim’s consent, the ACSC investigated the incident tracing the attack back to APT40’s activities, based on the data collected from the host-based sensors. Additionally, in March 2024, the New Zealand government implicated APT40 hackers for the Parliamentary Counsel Office and the Parliamentary Service breach back in 2021.
Upon further analysis of APT40 reflected in a dedicated advisory, cybersecurity experts state that hacking collective is mostly aimed at reconnaissance activities on networks of interest to identify potential targets for compromise. This ongoing surveillance allows the group to detect vulnerable, outdated, or unmaintained devices on these networks and quickly deploy the exploits.
APT40 seems to favor targeting vulnerable, public-facing infrastructures over methods requiring user engagement, like phishing campaigns, and prioritize acquiring valid credentials to facilitate follow-on activities. Notably, the APT40 seems to be a pro in quickly modifying and deploying exploits for new security flaws, actively surveilling networks to spot unpatched systems. Particularly, the advisory states that hackers promptly benefited from exploits in popular software such as Log4j, Atlassian Confluence, and Microsoft Exchange to target systems in the limelight.
Further analysis of the APT40 tradecraft shows that adversaries employ web shells for persistence during the earliest stages of the intrusion. Following gaining the initial foothold, the group tends to rely on outdated devices, such as SOHO routers, to channel malicious traffic and fly under the radar. Subsequent attack chain includes reconnaissance, privilege escalation, and lateral movement activities, leveraging RDP to capture credentials and dump valuable data.
To counteract such intrusions, security experts advise to deploy comprehensive logging solutions, enforce multi-factor authentication (MFA), establish a rigorous patch management protocol, upgrade outdated equipment, deactivate unnecessary services, ports, and protocols, and segment networks to safeguard sensitive information. Stay ahead of emerging threats and future-proof your organization’s cybersecurity posture by leveraging SOC Prime’s complete product suite for AI-powered Detection Engineering, Automated Threat Hunting, and Detection Stack Validation.




