How It Works
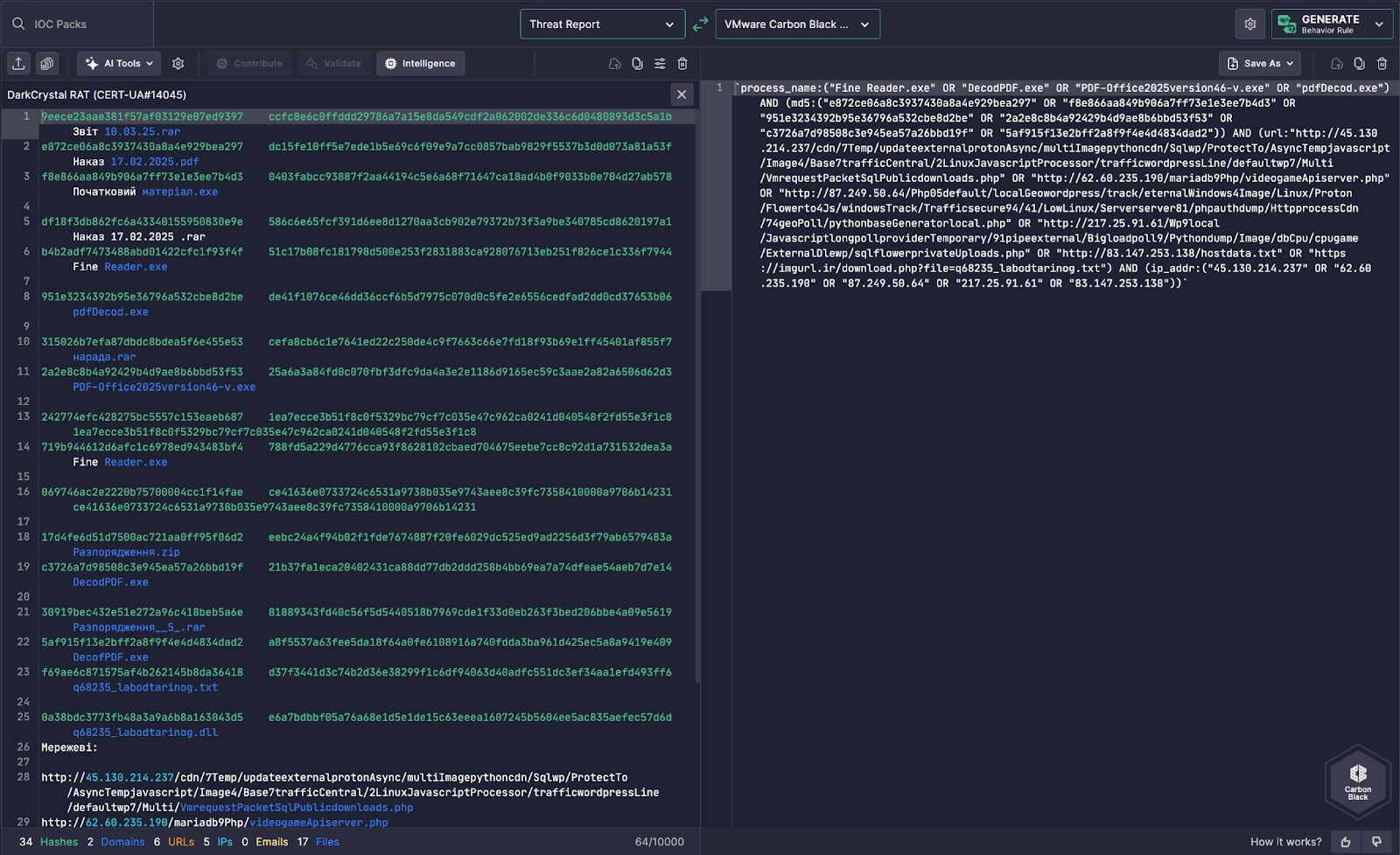
Uncoder AI processes threat reports like CERT-UA#14045 on DarkCrystal RAT and generates Carbon Black-compatible detection logic. This feature maps observed file hashes, execution patterns, and C2 infrastructure into a rule that’s ready to deploy within Carbon Black’s behavioral telemetry stack.
On the left, the threat report details the DarkCrystal campaign, including:
- Malicious file names (
Fine Reader.exe,pdfDecode.exe) - SHA256 hashes for droppers and RAT payloads
- Embedded infrastructure (e.g.,
45.130.214.237,62.60.235.190) - Known URL paths with embedded download scripts and traffic exfiltration components
Uncoder AI transforms these disparate IOCs into a tightly scoped query using Carbon Black’s event model.
Detection Logic Breakdown
process_name:("Fine Reader.exe" OR "DecodPDF.exe" OR "PDF-Office2025version46.v.exe" OR "pdfDecode.exe")
AND (
md5:("e8720e86ca8937...") OR
md5:("f8e86a48a9b06a...") OR
md5:("951e32343290b5...") OR
md5:("2ae8e804a92249...")
)
AND (
url:("http://45.130.214.237/cdn/Time/updateexternalprotonAsync/multiImagepythoncdn/SqIwp/..." OR
"http://62.60.235.190/mariadpPhp/videogameApiServer.php" OR
"http://87.249.50.64/Phploadhtm.php?id=qq8235_labdotarinoq.txt")
)
AND (
dst_ip:("45.130.214.237" OR "62.60.235.190" OR "87.249.50.64" OR "217.25.21.61" OR "83.147.253.138")
)
Components Mapped by AI
- Process Names:
Captures decoy executables mimicking document readers and PDF tools - File Hashes (MD5):
Targets known variants of droppers and RAT stagers - URLs and Path Patterns:
Includes JavaScript loaders, file exfiltration paths, and async PHP modules used for delivery or callback - Destination IPs:
Flags known attacker-controlled infrastructure tied to C2 operations
Why It’s Innovative
Writing detection rules for Carbon Black traditionally involves manually stitching together IOC elements, matching syntax, and testing field compatibility. Uncoder AI solves this by:
- Recognizing Carbon Black’s telemetry model (process, md5, url, dst_ip)
- Auto-aggregating threat intelligence into logical groupings
- Generating a production-ready rule from unstructured IOC reports
This eliminates the need for context-switching between PDFs, spreadsheets, and the Carbon Black console.
Operational Value
For Carbon Black defenders and incident response teams:
- Accelerated IOC-to-Rule Pipeline
Go from CERT-UA threat reports to Carbon Black rules in minutes, not hours - High-Fidelity Threat Matching
Simultaneously match known malware hashes, behavior patterns, and infrastructure - Improved C2 Discovery
Flag outbound connections to domains and IPs used for DarkCrystal RAT staging and communication
Uncoder AI makes threat intel actionable in Carbon Black by automating the most technical and error-prone parts of detection rule authoring.
Detection Focus: Password File Access via Notepad
This rule tracks when:
- A process launch is triggered by explorer.exe
- The launched process is notepad.exe
- The command line references filenames containing “password” with extensions like
.txt,.csv,.doc, or.xls
- Insider access to plaintext credentials
- Unauthorized snooping of exported password lists
- Misuse of basic OS tools for reconnaissance or data leakage
How AI-generated Decision Tree Helped
Uncoder AI automatically transformed the UDM query into a structured logic tree, revealing:
- Event Type Check – Only PROCESS_LAUNCH events are considered
- Parent Process Filter – Must be
explorer.exe(the user manually opens the file) - Launched Process Filter – Must be notepad.exe
- Filename Match – Command line must include terms like
password.txt,password.csv, etc.
Each branch of the logic is clearly explained, with regex patterns visualized as OR conditions under a single node. This reduces friction in understanding and documenting what’s being detected—and why.




