Right after Microsoft disclosed an actively exploited Office zero-day (CVE-2026-21509) on January 26, 2026, CERT-UA reported UAC-0001 (APT28) leveraging the vulnerability in the wild. The russia-backed threat actor targeted organizations in Ukraine and the EU with malicious Office documents, and metadata shows one sample was created on January 27 at 07:43 UTC, illustrating the rapid weaponization of CVE-2026-21509.
Detect UAC-0001 aka APT28 Activity Based on the CERT-UA#19542 Alert
APT28 (UAC-0001) has a long record of conducting cyber operations aligned with russian state interests, with a persistent focus on Ukraine and its allied partners. Ukraine frequently serves as an initial testing environment for newly developed tactics, techniques, and procedures that are later scaled to broader international targets.
The latest UAC-0001 campaign in the limelight follows the same pattern. According to CERT-UA#19542, UAC-0001 targeted Ukrainian state bodies with malicious Office documents exploiting CVE-2026-21509 to deploy the COVENANT framework. The same attack pattern was later observed against EU organizations, demonstrating rapid operational expansion beyond Ukraine.
Sign up for the SOC Prime Platform to proactively defend your organization against UAC-0001 (APT28) attacks exploiting CVE-2026-21509. Just press Explore Detections below and access a relevant detection rule stack, enriched with AI-native CTI, mapped to the MITRE ATT&CK® framework, and compatible with a wide range of SIEM, EDR, and Data Lake technologies.
Security experts can also use the “CERT-UA#19542” tag based on the relevant CERT-UA alert identifier to search for the detection stack directly and track any content changes. For more rules to detect attacks related to the UAC-0001 adversary activity, security teams can search the Threat Detection Marketplace library leveraging the “UAC-0001” or “APT28” tags based on the group identifier, as well as the relevant “CVE-2026-21509” tag addressing the Microsoft Office zero-day exploitation.
Additionally, users can refer to a dedicated Active Threats item on the UAC-0001 (APT28) latest attacks to access the AI summary, related detection rules, simulations, and the attack flow in one place.
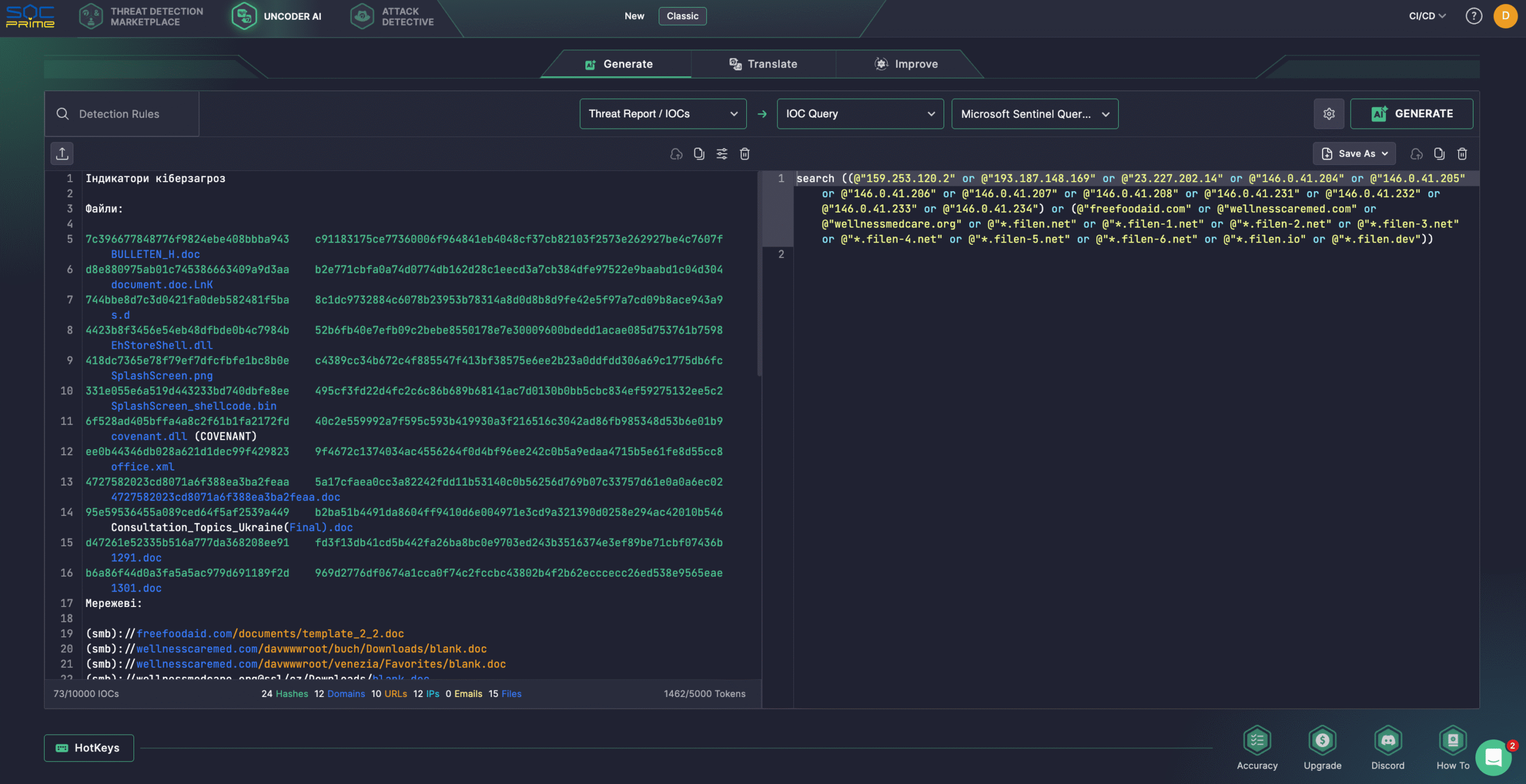
Security teams can also rely on Uncoder AI to create detections from raw threat reports, document and optimize code, and generate Attack Flows. Additionally, cyber defenders can easily convert IOCs from the latest CERT-UA#19542 alert into performance-optimized queries compatible with your security stack.
Analyzing UAC-0001 (APT28) Attacks Exploiting CVE-2026-21509
In late January 2026, CERT-UA observed a series of targeted cyber attacks attributed to UAC-0001 (APT28) that leveraged an actively exploited Microsoft Office vulnerability tracked as CVE-2026-21509. The malicious activity emerged shortly after Microsoft publicly disclosed the flaw and was initially directed at Ukrainian government entities before expanding to organizations across the European Union.
To establish initial access, attackers distributed specially crafted Microsoft Word documents exploiting CVE-2026-21509. One document, titled “Consultation_Topics_Ukraine(Final).doc,” referenced COREPER, the Committee of Permanent Representatives of the EU, which prepares decisions and coordinates policy among EU member states. Although the file became publicly accessible on January 29, metadata analysis showed it had been created on January 27 (one day after Microsoft’s advisory), indicating rapid weaponization of the vulnerability.
In parallel, CERT-UA received reports of phishing emails impersonating official correspondence from the Ukrainian Hydrometeorological Center. These messages, sent to more than 60 recipients primarily within central executive authorities of Ukraine, contained malicious DOC attachments. When opened in Microsoft Office, the documents established a network connection to an external resource over WebDAV and downloaded a shortcut file containing code designed to retrieve and launch an executable file.
Successful execution of the downloaded payload results in the creation of a malicious DLL file, EhStoreShell.dll, masquerading as the legitimate Enhanced Storage Shell Extension library, and an image file (SplashScreen.png) containing shellcode. The attack also modifies the Windows registry path for CLSID {D9144DCD-E998-4ECA-AB6A-DCD83CCBA16D}, implementing COM hijacking, and creates a scheduled task named OneDriveHealth.
Scheduled execution of the task causes the explorer.exe process to terminate and restart, which (due to the COM hijacking) ensures the loading of EhStoreShell.dll. The DLL executes shellcode from the image file, ultimately resulting in the launch of the COVENANT framework. Command-and-control communications for COVENANT relied on legitimate cloud storage infrastructure provided by Filen (filen.io).
Toward the end of January 2026, CERT-UA identified additional documents using the same exploit chain and delivery mechanisms in attacks against EU-based organizations. Technical overlaps in document structure, embedded URLs, and supporting infrastructure suggest these incidents were part of a coordinated UAC-0001 (APT28) campaign, demonstrating the rapid scaling of the operation beyond its initial Ukrainian targets.
Given the active exploitation of a Microsoft Office zero-day and the challenges many organizations face in promptly applying patches or mitigations, further abuse of CVE-2026-21509 is expected in the near term.
To reduce the attack surface, organizations should implement the mitigation measures outlined in Microsoft’s advisory, including recommended Windows registry configurations. In addition, as UAC-0001 (APT28) leverages legitimate Filen cloud infrastructure for COVENANT command-and-control operations, network interactions with Filen-related domains and IP addresses should be restricted or placed under enhanced monitoring.
Additionally, security experts can rely on SOC Prime’s AI-Native Detection Intelligence Platform, which equips SOC teams with cutting-edge technologies and top cybersecurity expertise to stay ahead of APT28 attacks while maintaining operational effectiveness.
MITRE ATT&CK Context
Leveraging MITRE ATT&CK offers in-depth insight into the latest UAC-0001 (APT28) attacks leveraging CVE-2026-21509 exploit to target Ukrainian and EU entities. The table below displays all relevant Sigma rules mapped to the associated ATT&CK tactics, techniques, and sub-techniques. Tactics Techniques Sigma Rule Persistence Scheduled Task/Job: Scheduled Task (T1053.005) Event Triggered Execution: Component Object Model Hijacking (T1546.015) Defense Evasion Masquerading: Match Legitimate Resource Name or Location (T1036.005) Command and Control Application Layer Protocol: Web Protocols (T1071.001) Ingress Tool Transfer (T1105) Impact Service Stop (T1489)




