The rise of AI-powered attacks against critical business systems marks a new and alarming phase in cyber threats. While adversaries are advancing their methods, continuously exploring ways to weaponize AI for malicious purposes, the future of cybersecurity will largely depend on how seamlessly AI is combined with other emerging technologies. Cybersecurity experts have recently uncovered a newly emerging AI-driven ransomware strain, tracked as FunkLocker and used by FunkSec operators, which employs double extortion techniques and has already impacted over 100 global organizations across diverse industry sectors.
Detect FunkLocker Ransomware by FunkSec
Organizations face a new era of cyber risk as attackers increasingly weaponize artificial intelligence to breach critical business assets. Gartner’s 2025 Top Cybersecurity Trends highlights how generative AI is reshaping the threat landscape, creating both new vulnerabilities and opportunities to build more adaptive defense strategies. Complementing this, recent research from Cybersecurity at MIT Sloan and Safe Security (spanning 2,800 ransomware incidents) reveals that four out of five attacks now leverage AI for malicious purposes, from crafting sophisticated malware and phishing campaigns to deploying deepfake-enabled social engineering tactics.
One of the latest examples is FunkSec, an AI-assisted ransomware strain, which underscores the urgent need for enterprises to go beyond traditional defenses and adopt flexible, AI-informed security workflows capable of countering the next generation of threats.
Register for the SOC Prime Platform to access the latest CTI & curated detection rules, enabling you to immediately identify malicious activity associated with FunkLocker attacks. The detection stack is backed by a complete product suite for AI-powered detection engineering, automated threat hunting, and advanced threat detection. Just press the Explore Detections button below to start.
All detection algorithms can be used across multiple SIEM, EDR, and Data Lake solutions, and are aligned with MITRE ATT&CK® for streamlined threat research. In addition, each vendor-agnostic Sigmac rule is enriched with actionable metadata, such as CTI links, attack timelines, audit configurations, and more cyber threat context.
Security engineers also use Uncoder AI acting as an AI co-pilot, supporting detection engineers end-to-end while streamlining workflows and enhancing coverage. With Uncoder, defenders can instantly convert IOCs into custom hunting queries, craft detection code from raw threat reports, generate Attack Flow diagrams, leverage AI-driven query optimization, and more. For instance, below is the Attack Flow diagram based on the latest ANY.RUN’s research.
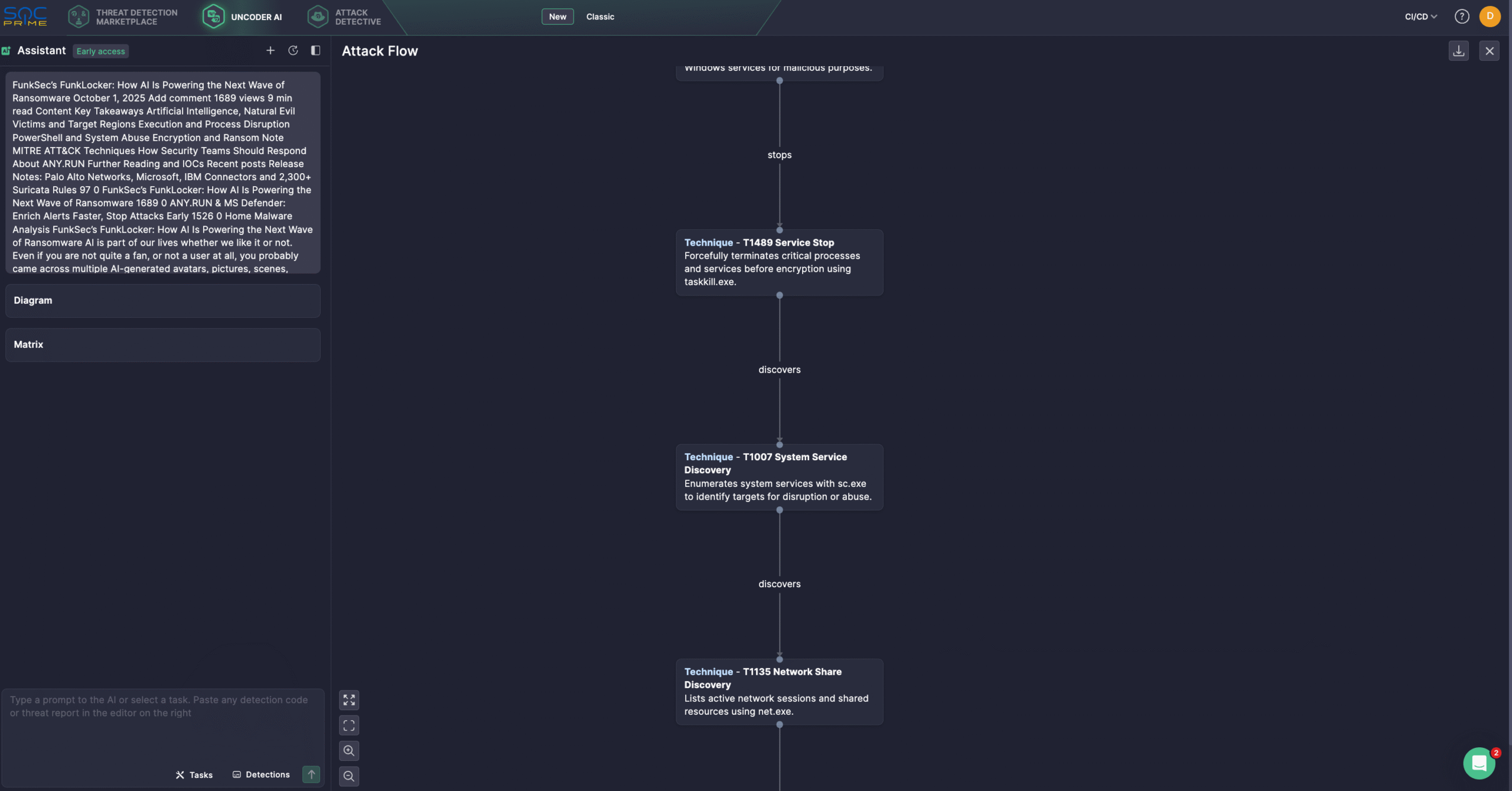
FunkLocker Ransomware Analysis
AI-driven malware is not a new phenomenon—defenders have already observed campaigns leveraging AI-themed lures to spread strains such as CyberLock, Lucky_Gh0$t, and Numero, along with Koske, a newly identified AI-generated malware targeting Linux systems. Cybersecurity experts have recently uncovered a relatively new AI-assisted ransomware strain, FunkLocker used by FunkSec ransomware maintainers, which surfaced in late 2024. According to ANY.RUN’s research, the FunkSec ransomware group has already compromised more than 100 organizations using its own data leak site.
FunkSec ransomware team employed double extortion tactics, pairing data theft with file encryption to coerce victims into paying. Unlike many established ransomware gangs, FunkSec has demanded unusually modest ransoms, sometimes as low as $10,000, while also selling stolen data at discounted prices to third parties.
In early winter 2024, FunkSec launched a data leak site to streamline its operations. The site not only publishes victim announcements but also features a custom DDoS tool and its own ransomware strain, which is offered under a RaaS model.
Most of FunkSec’s victims have been identified in the U.S., India, Italy, Brazil, Israel, Spain, and Mongolia. Some members of the RaaS group have been linked to hacktivist operations, highlighting the ongoing overlap between hacktivism and cybercrime. Evidence that the group may be engaging in hacktivist activities includes the use of DDoS tools, as well as remote management utilities, like JQRAXY_HVNC, and password generation, such as funkgenerate.
FunkSec ransomware variants, including FunkLocker, exhibit coding traces that resemble “AI snippet” patterns. This makes the malware relatively easy to assemble, but it is often inconsistent in execution and reliability. The ransomware exists in several builds, some of which are barely operational, while others incorporate advanced techniques such as anti-virtual machine detection. This inconsistency highlights a rapid but unstable development process.
FunkLocker attempts to shut down processes and services using predefined lists. While this sometimes results in unnecessary errors, the approach still achieves significant system disruption and prepares the environment for encryption. Legitimate Windows utilities, including taskkill.exe, sc.exe, net.exe, and PowerShell, are repurposed by FunkSec operators to terminate applications, disable protective measures, and facilitate file encryption.
Unlike many contemporary ransomware families that rely on C2 infrastructure, FunkSec operates entirely offline. Files are encrypted locally and marked with the .funksec extension.
The malware attempts to drop ransom notes directly on the desktop. However, due to frequent system instability, victims are often unable to view the notes until they perform a reboot. FunkSec exhibits signs of careless operational practices, including the reuse of Bitcoin wallets and reliance on locally derived or hardcoded encryption keys.
Check Point researchers noted that the rapid development of the group’s tools, including the ransomware encryptor, was likely AI-assisted, which helped accelerate iteration despite the apparent lack of technical expertise from the author.
The newest ransomware version, FunkSec V1.5, is written in Rust and was uploaded to VirusTotal from Algeria. Analysis of older variants shows references to FunkLocker and Ghost Algeria in ransom notes. Most samples were also uploaded from Algeria, possibly by the developer, suggesting that the threat actor is likely based in that country.
Potential FunkLocker ransomware mitigation steps, along with similar AI-assisted threats, require shifting from static indicators to behavioral detection, ensuring comprehensive and rapid visibility into the full execution chain to reduce downtime, as well as leveraging AI-driven platforms to close the skill gap and accelerate the technology stack for next-gen cyber defense. SOC Prime’s complete product suite can be a feasible solution to help organizations take their AI-powered cyber defense capabilities to the next level. Backed by top cybersecurity expertise and AI, organizations can rely on an extensive library of behavioral detections, automated capabilities, and AI-native threat intelligence for future-proof cyber defense against emerging ransomware attacks and other sophisticated threats.




