The vulnerability management lifecycle is an essential process for defending against the escalating number of cyber threats in our modern digital era. In 2023 alone, over 30,000 new vulnerabilities were spotted, with a 42% increase observed in 2024, underscoring the urgent need for effective coping strategies. As adversaries, including sophisticated state-sponsored groups like APT40, rapidly exploit these security flaws, organizations must adopt a structured methodology for vulnerability management.
The vulnerability management lifecycle is aimed at addressing security gaps within an organization’s IT infrastructure. The process initiates with the detection of potential flaws via continuous system monitoring. Following detection, these security weaknesses are evaluated for their potential impact and exploitability, allowing for prioritized remediation. The concluding phases encompass implementing the necessary fixes and performing detailed reporting and documentation, establishing a proactive defense against the latest threats.
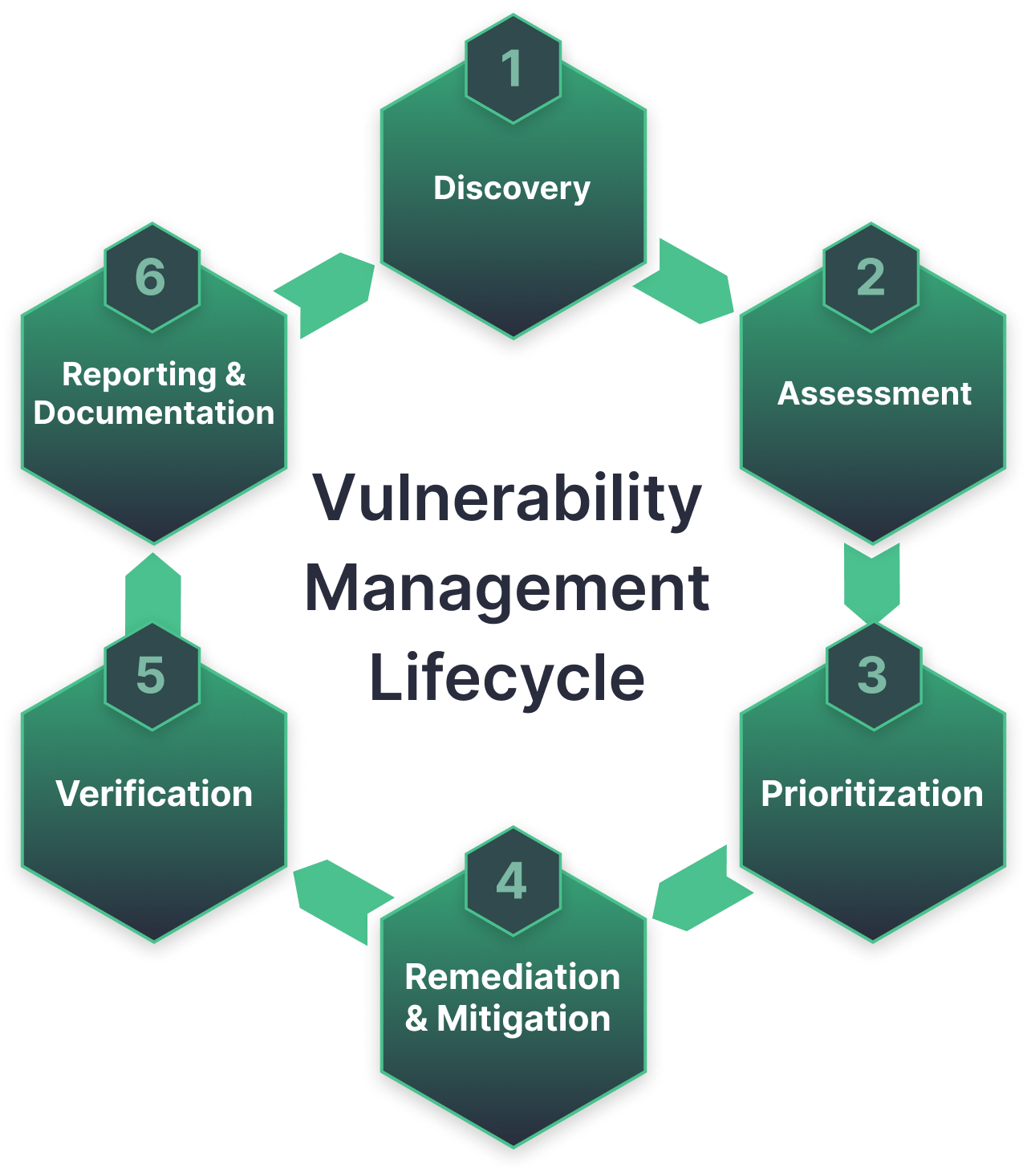
The lifecycle normally encompasses six key stages aimed at maintaining a bullet-proof security stance:
- Discovery. Listing all IT assets that might contain potential flaws and put organization at risk.
- Assessment. Evaluating the seriousness and potential consequences of identified security flaws.
- Prioritization. Ranking security gaps depending on their risk factors to focus remediation efforts effectively.
- Remediation & Mitigation. Deploying fixes or patches to resolve vulnerabilities and instituting mitigation strategies to minimize their impact when full resolution is not achievable.
- Verification. Reassessing and retesting to make sure that security issues have been resolved effectively.
- Reporting & Documentation. Documenting all the ins and outs of the vulnerability management flow and its results for stakeholders.
By continuously running the six stages above, security teams can build a robust defense while minimizing the risks of intrusions.
Vulnerability Management Lifecycle Phases
Discovery
The initial step involves a comprehensive identification of all assets within the network that could harbor security flaws. Achieving a comprehensive understanding of the organization’s IT infrastructure is vital to verify no asset is neglected, thereby preventing potential infection vectors.
To make sure security teams are collecting all the relevant data to enable comprehensive threat discovery, they might rely on SOC Prime’s Attack Detective. The solution enables organizations to fortify their SIEM posture with an actionable plan aimed at maximizing threat visibility and addressing detection coverage gaps, obtain prioritized SIEM use cases, easily configurable and ready-to-deploy as low-noise and high-value alerts, and deliver real-time, researched, and packaged threat hunting capability to eliminate the risks of breaches.
Assessment
Once all components are cataloged and classified, these assets undergo scanning and vulnerability assessment to pinpoint those at risk. This phase entails an evaluation of identified issues to determine their potential impact on the organization’s security stance. Methods like penetration testing and threat modeling are frequently used to replicate potential attacks and gauge the actual risks posed by these security weaknesses.
With the continuously growing numbers of new vulnerabilities uncovered in the popular software, proactive detection of vulnerability exploitation remains one of the most common security use cases. SOC Prime’s Threat Detection Marketplace curates the world’s largest Detection-as-Code library of algorithms, addressing any cyber attack or emerging threat under a 24-hour SLA, including over 1,000 pieces of SOC content to detect vulnerability exploitation.
Prioritization
After discovering security gaps, they need to be evaluated and prioritized based on their severity, potential impact, and exploitability. Normally, SOC teams employ the following criteria at the this stage:
- Asset Value. Based on the first stage assessment, security experts should consider the value of the infrastructure component containing the security issue.
- CVE & CVSS ratings. This can include MITRE’s list of Common Vulnerabilities and Exposures (CVE) or the Common Vulnerability Scoring System (CVSS). Yet, the criticality rating itself is not sufficient to make decisions since the issue might be present in low-value assets or have limited business impact.
- Possible Impact on Business Activities. While prioritizing remediation efforts, securing teams should precisely determine how vulnerabilities can affect business operations, including disruption to services, data leakage, and financial losses.
- Risk of Exploitation. This refers to the probability that a flaw within an IT system will be discovered and used by a threat actor to cause harm.
- Exposure. This represents how accessible the vulnerability is to advesaries. If the vulnerable asset is publicly accessible, it is more likely to be targeted.
This phase is essential for optimizing resource allocation and concentrating efforts on significant threats. To assist defenders in effectively operationalizing threat intel, SOC Prime’s Threat Detection Marketplace equips defenders with complete threat context linked to detection algorithms addressing the latest or existing threats, including CVE descriptions, exploit POCs, CTI and MITRE ATT&CK references, mitigation, and media links.
Remediation & Mitigation
Once security teams have a prioritized list of security flaws, the next step is to tackle the potential threats. There are three approaches to vulnerability resolution:
- Remediation. Addressing a vulnerability to thwart its exploitation entails measures such as patching an operating system bug, rectifying a misconfiguration, or eliminating a vulnerable asset from the network. Nonetheless, remediation isn’t always feasible. Sometimes, complete solutions aren’t immediately available, like with zero-day vulnerabilities. In other instances, the remediation process may be excessively resource-intensive.
- Mitigation. It encompasses strategies designed to complicate an attacker’s ability to exploit a vulnerability or to lessen the damage caused by its exploitation, without completely resolving the security gap. For example, enforcing more rigorous authentication and authorization measures within a web application can hinder attackers from compromising accounts. Similarly, crafting incident response plans for identified vulnerabilities can help mitigate the adverse effects of cyber incidents. Security teams frequently resort to mitigation when comprehensive remediation is either unattainable or prohibitively expensive.
- Acceptance. In very limited instances, some vulnerabilities are deemed so low-impact or improbable to be exploited that addressing them may not justify the cost. In such cases, the organization might choose to accept the risk posed by the vulnerability.
Verification
To verify the success of intervention and mitigation, the SOC team conducts follow-up scans and tests on the recently addressed assets. These audits aim to confirm that all identified vulnerabilities have been resolved and that no new issues have emerged from the fixes.
In addition to this focused reassessment, the security team also conducts a broader network review. This includes identifying any new vulnerabilities that may have arisen since the last scan, evaluating the relevance of outdated mitigations, and noting any other changes that could require further intervention. The outcomes from these activities offer crucial insights for the subsequent phase of the vulnerability management lifecycle.
Reporting & Documentation
In the concluding phase, security teams meticulously record the outcomes of the latest cycle, detailing the discovered vulnerabilities, the remedial actions taken, and the results achieved. These detailed reports are then disseminated to key stakeholders, such as executives, asset managers, and compliance officers.
Furthermore, the security team undertakes a comprehensive evaluation of the cycle’s performance. This includes scrutinizing critical metrics like mean time to detect (MTTD), mean time to respond (MTTR), the count of critical vulnerabilities, and recurrence rates. Tracking these metrics over time establishes a performance benchmark for the vulnerability management program and identifies areas needing improvement. The insights gained from each cycle are used to refine and enhance future efforts.
By diligently following these stages, organizations can adopt a proactive stance on cybersecurity, effectively identifying and addressing potential vulnerabilities before they can be exploited by malicious entities.
Benefits of Vulnerability Management Lifecycle
Implementing a vulnerability management lifecycle enhances an organization’s cybersecurity strategy, bolstering its capacity to protect assets and maintain strong defenses. The lifecycle offers a set of benefits that collectively contribute to a more secure and resilient IT environment.
Comprehensive Visibility Based on Data-Driven Insights. Regular vulnerability scanning and timely patching significantly impede attackers from breaching systems. This allows security teams to systematically detect and evaluate potential weaknesses, offering critical data for informed security and risk management decisions. This thorough comprehension enables the tailoring of security measures to address specific vulnerabilities, thus improving overall risk mitigation strategies.
Proactive Cyber Defense. Strong vulnerability management practices enable organizations to address and mitigate vulnerabilities before attackers can exploit them. This proactive stance reduces the likelihood of successful attacks, minimizes potential damage, and enhances the organization’s overall security posture. By staying ahead of potential threats and timely identifying security blindspots that might impact the organization’s security, organizations can maintain a robust defense, effectively securing their assets and data against cyber attacks of any scale and complexity.
Optimized Resource Allocation. Identifying and mitigating security risks helps organizations minimize system downtime and safeguard their data. Improving the vulnerability management process also reduces recovery time after incidents. Integrating the vulnerability management lifecycle into the cybersecurity strategy allows for more efficient allocation of time and money by prioritizing security weaknesses based on risk and impact. This ensures that organization’s resources focus on the most critical issues, resulting in more effective and efficient vulnerability management.
Structured Approach to Validating Security Measures. The vulnerability management lifecycle equips security teams with a standardized process to verify the effectiveness of controls and remediation efforts, ensuring continuous improvement of security measures. This structured approach produces more reliable results, allows organizations to automate crucial workflows, and maximizes the value of security investments. Ongoing validation helps maintain a robust security posture and adapt to the constantly evolving cybersecurity landscape.
Vulnerability Management Lifecycle According to the NIST Guidelines
For decades, enterprise patch management has been a disputable issue, with security and business/mission personnel often holding conflicting views. Organizations frequently face the challenge of balancing the trade-offs between rapid deployment and thorough testing. Deploying patches swiftly reduces the window of opportunity for attackers but raises the risk of operational disruptions due to insufficient testing. NIST has released its Special Publication 800-40r4, Guide to Enterprise Patch Management Planning: Preventive Maintenance for Technology, aimed to help CISOs, cybersecurity executives, and others who manage organizational risk associated with software usage address these challenges and smoothly adopt a structured approach to effective patch management.
The guide serves as an extensive manual for creating and executing a robust enterprise patch management program. It emphasizes a methodical approach that underscores the need for Asset Discovery and Vulnerability Assessment to identify and understand potential vulnerabilities. The guide highlights the importance of prioritizing assets and vulnerabilities, which helps in developing an informed and effective Patching Program.
The NIST SP 800-40r4 presents patching as an essential element of preventive maintenance for computing technologies, viewing it as a necessary expense for organizations to fulfill their missions. It addresses common challenges in enterprise patch management and recommends building a comprehensive strategy to streamline and operationalize the patching process while enhancing risk reduction. Implementing preventive maintenance through enterprise patch management is crucial for preventing compromises, data breaches, operational disruptions, and other negative incidents.
The NIST’s Special Publication details the need for prioritizing identified vulnerabilities through structured risk assessments, leading to efficient Remediation and Mitigation Actions. This ensures targeted patch deployment, taking into account maintenance plans and exceptions, to address vulnerabilities precisely.
Additionally, the guide stresses the importance of Validation and Monitoring to verify patch effectiveness, supported by strong Reporting and Continuous Improvement mechanisms that continuously enhance patching processes.
By incorporating these essential components, the publication provides in-depth guidance, delivering valuable insights and actionable metrics that enable organizations to strengthen their cybersecurity stance, ensure ongoing improvement, and effectively respond to the evolving threat landscape.
With the constantly expanding attack surface, it’s imperative for progressive organizations to find a future-proof vulnerability management solution that facilitates resource optimization and consolidates visibility, assessment, and remediation capabilities. By relying on SOC Prime’s platform for collective cyber defense based on global threat intelligence, crowdsourcing, zero-trust, and AI, organizations can accelerate their vulnerability management lifecycle and make sure they can proactively defend against critical threats and eliminate the risks of data breaches.




